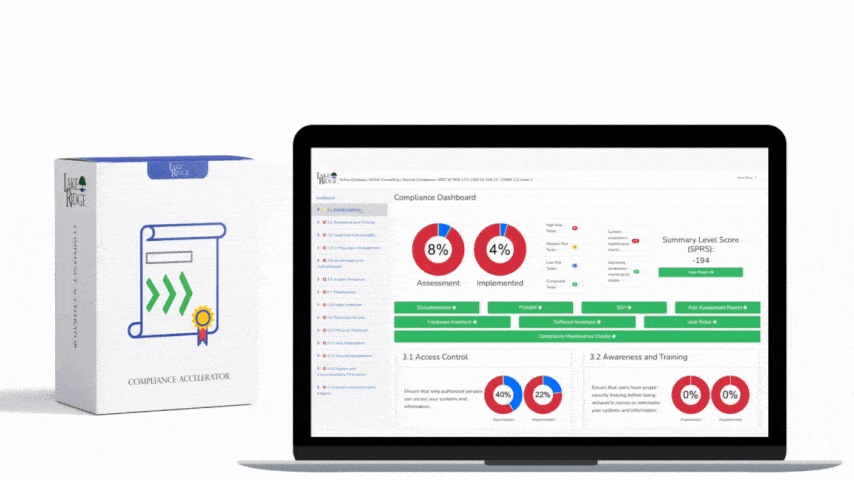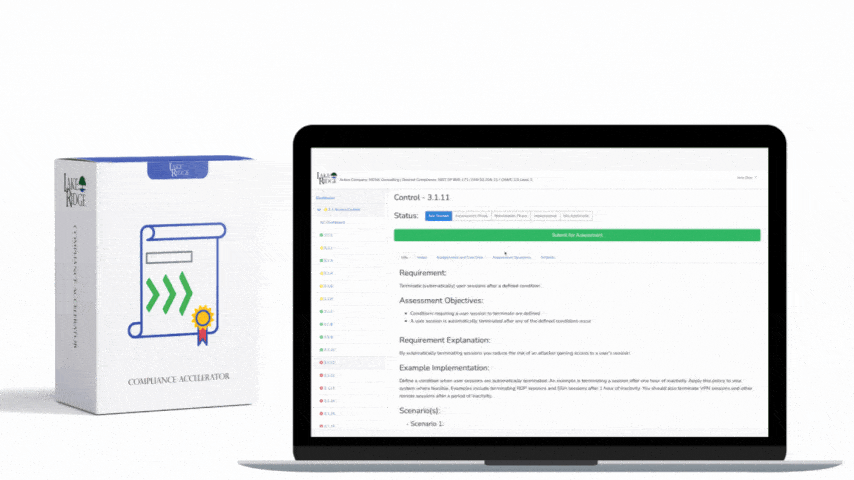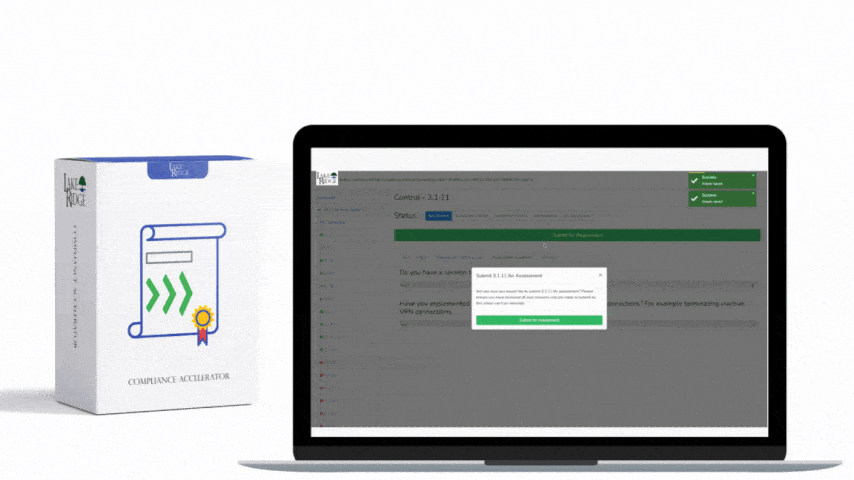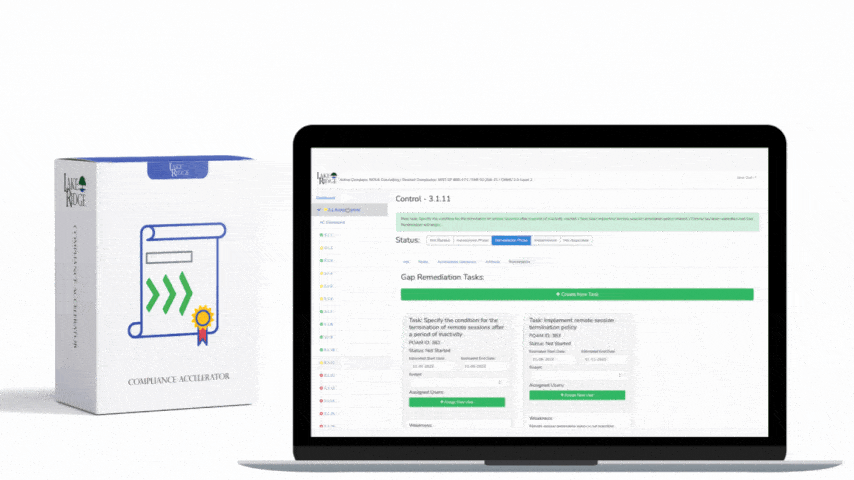
CMMC 1.0 Practice AC.2.011 Requirement:
Authorize wireless access prior to allowing such connections.
CMMC 1.0 AC.2.011 Requirement Explanation:
WiFi networks pose additional risk because they are easy to access by a wide range of devices and access to them is less restricted by physical location. This risk can be reduced by only allowing authorized devices to connect to wireless networks.
Example CMMC 1.0 AC.2.011 Implementation:
Define the types of devices allowed onto your company's networks and only allow them access to your WiFi. For example you decide to only allow company owned devices onto your WiFi network. You can enforce this policy via a technical control (e.g. Mac address filtering or 802.1X authentication). If you have guests or employees that need to use WiFi you can setup a separate WiFi network for them. Create an acceptable use policy that specifies the usage restrictions for your WiFi network. Think of the acceptable use policy you accept when you access WiFi at a hotel.
CMMC 1.0 AC.2.011 Scenario(s):
- Scenario 1:
A visitor comes to your facility and wants to access the WiFi. You connect him to the guest WiFi network because only your company devices are allowed on the corporate WiFi network.
- Scenario 2:
John, an employee at your company attempts to connect his personal laptop to your WiFi network. Because you have configured 802.1X authentication for your corporate network he is unable to connect his personal device to it.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you