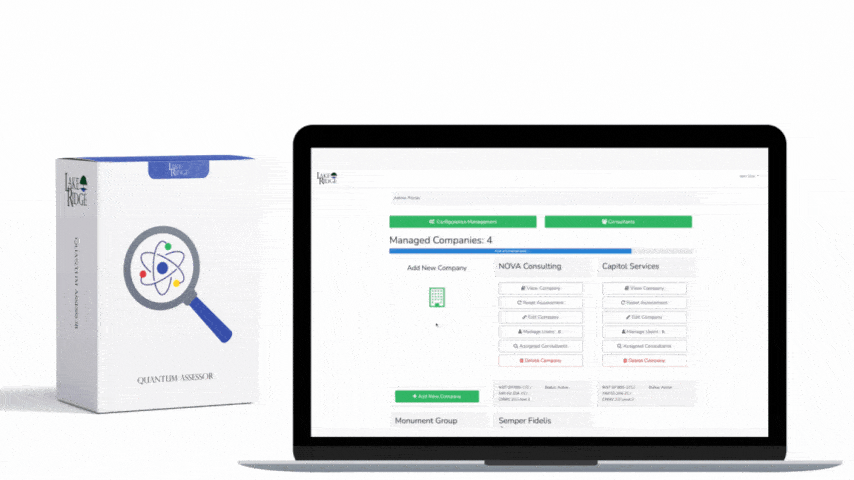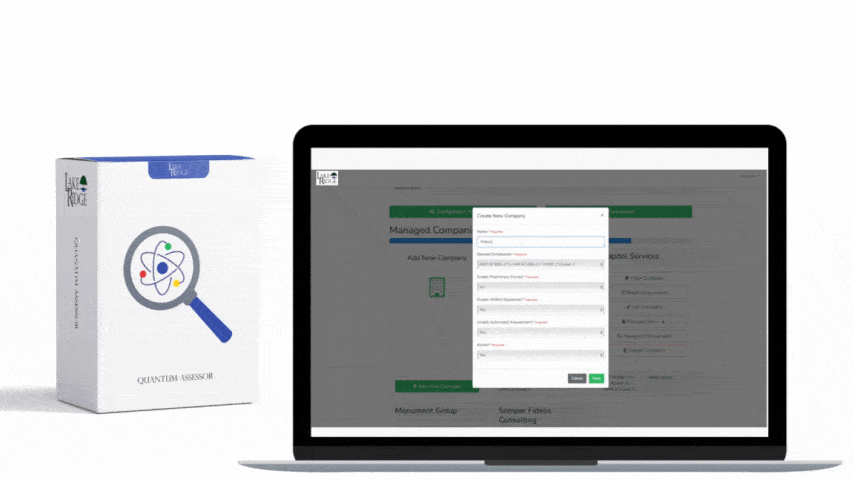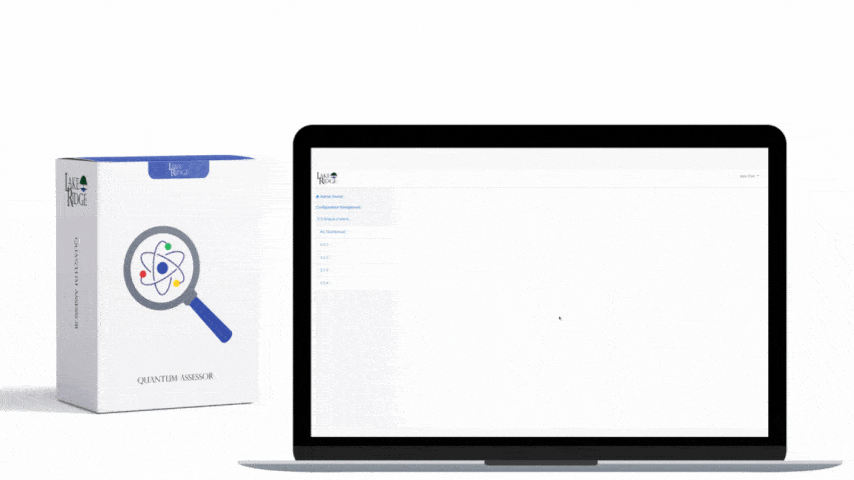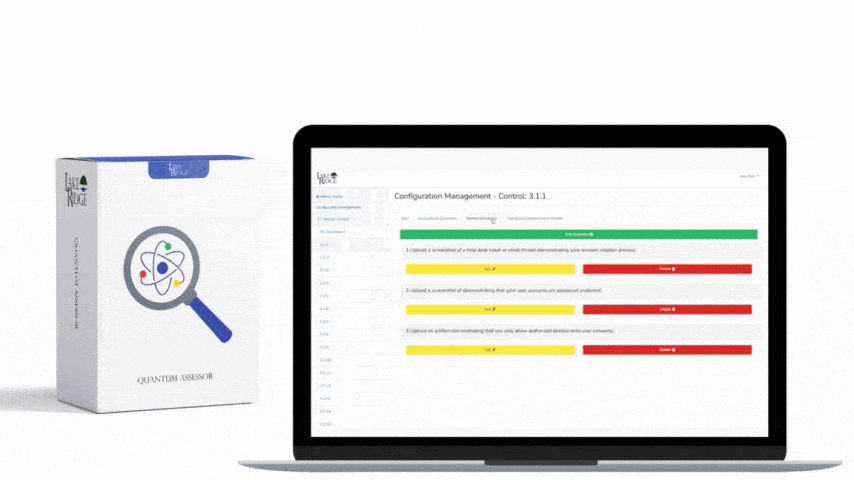
CMMC 1.0 Practice AU.3.049 Requirement:
Protect audit information and audit logging tools from unauthorized access, modification, and deletion.
CMMC 1.0 AU.3.049 Requirement Explanation:
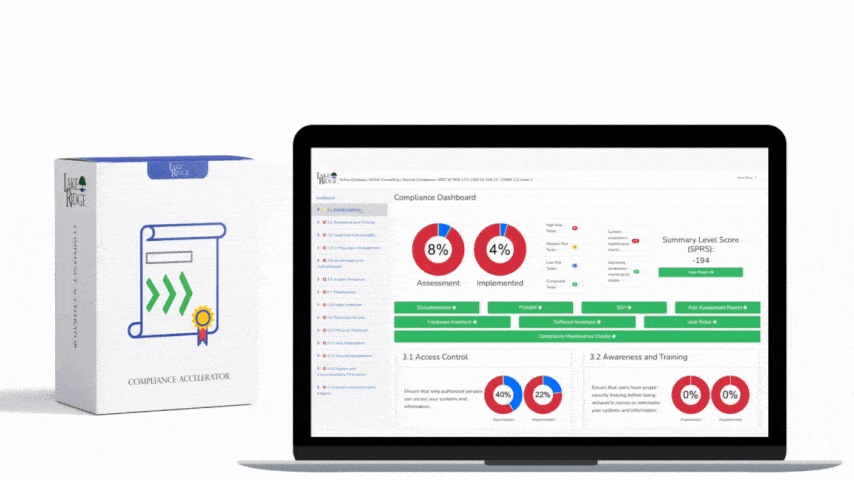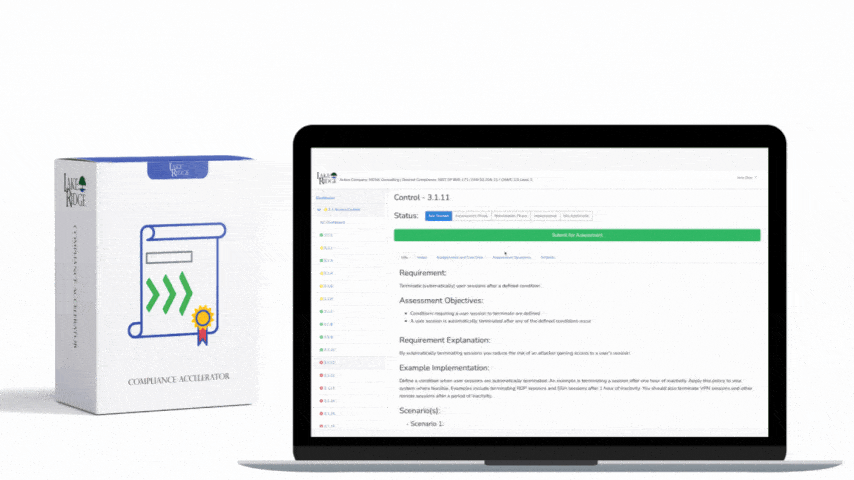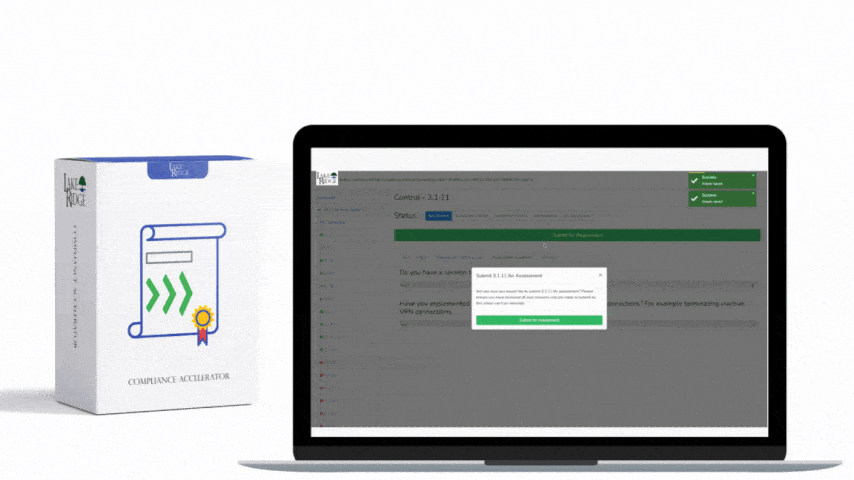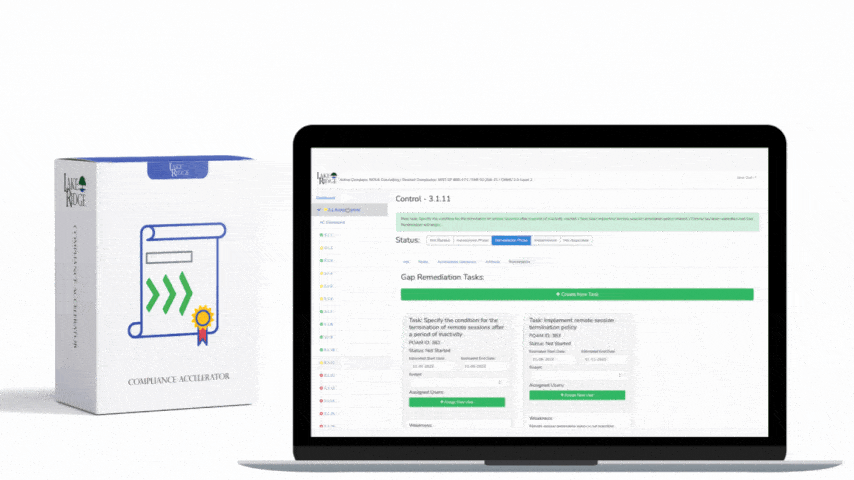
Audit logs are critical for identifying security incidents and policy violations hence the need to protect them. Protection entails protecting their confidentiality (encrypted storage), integrity (preventing users from modifying them), and availability (backing up your syslog server).
Example CMMC 1.0 AU.3.049 Implementation:
Forward the audit logs on your systems to your syslog server. Prevent users from deleting audit logs from their systems by revoking their local admin rights. Only allow authorized persons access to your syslog server and SIEM. Create backups of your syslog server.
CMMC 1.0 AU.3.049 Scenario(s):
- Scenario 1:
To protect audit information you prevent users from modifying audit logs on their system by revoking their admin privileges. You send logs to your syslog server as they are created. You only allow personnel with auditing responsibilities to access the syslog server. When system admins need to conduct maintenance they are supervised. You create backups of your syslog server to ensure the availability of audit logs.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you