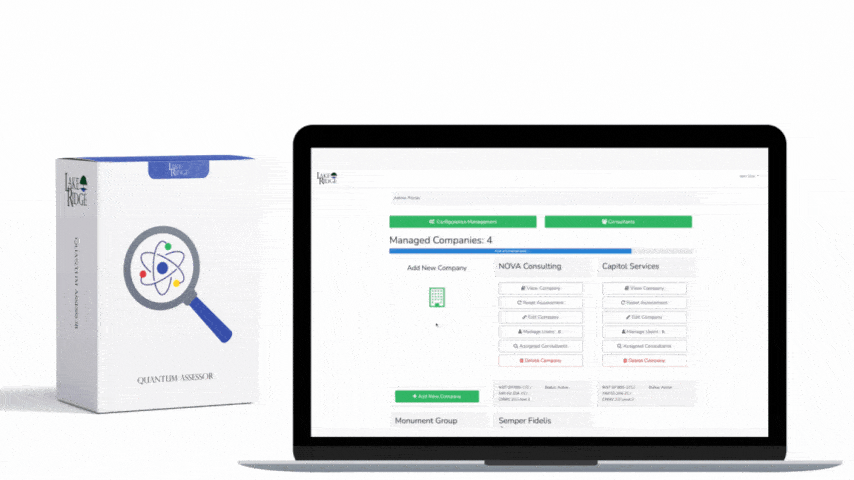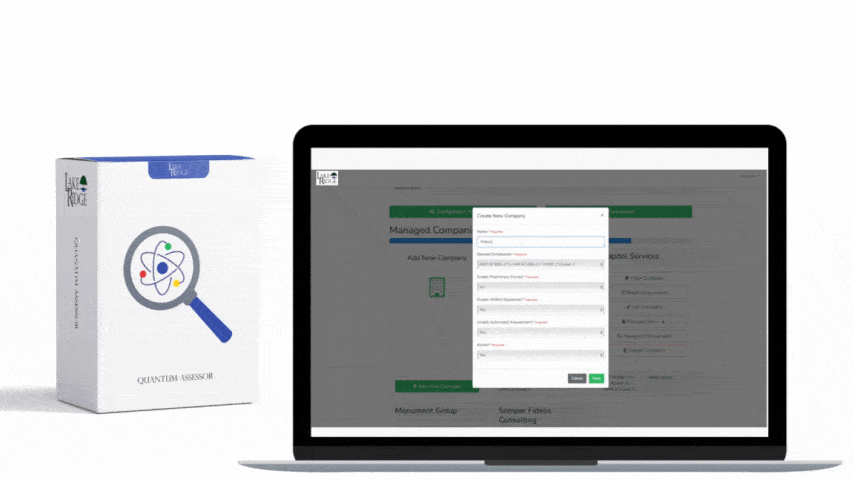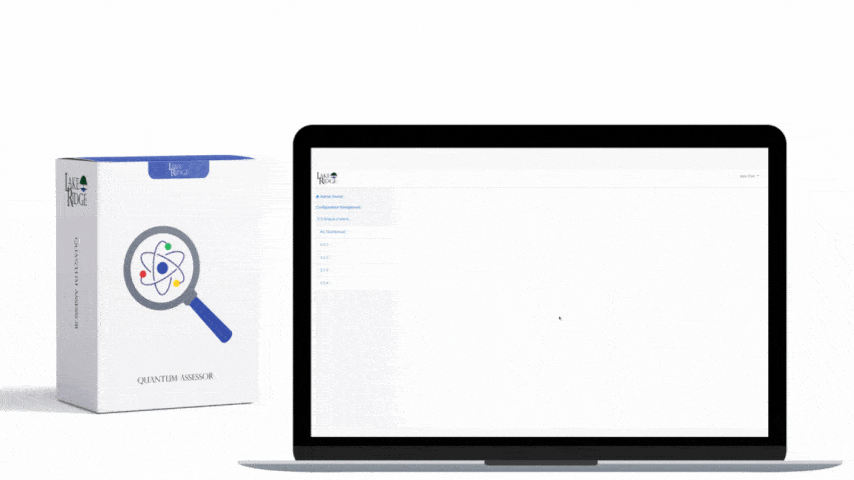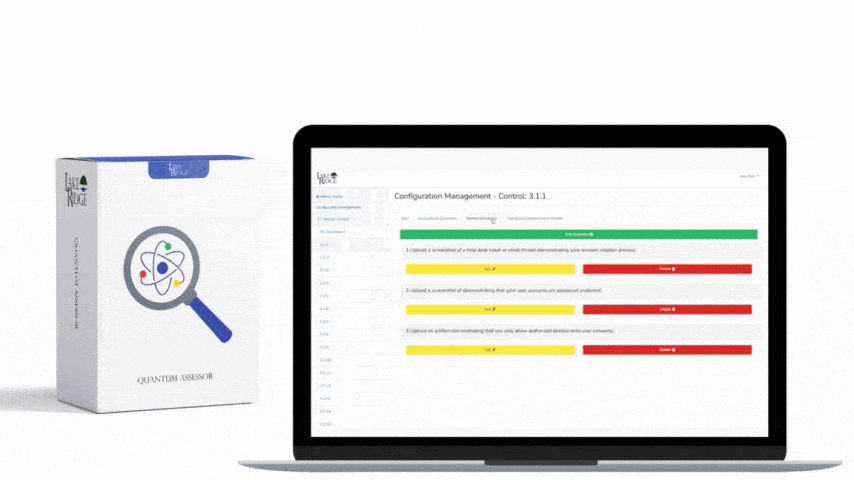
CMMC 1.0 Practice CA.3.162 Requirement:
Employ a security assessment of enterprise software that has developed internally, for internal use, and that has been organizationally defined as an area of risk.
CMMC 1.0 CA.3.162 Requirement Explanation:
If your company has developed any software internally and uses it internally it needs to undergo a security assessment. The assessment can be completed by your employees or by a third party.
Example CMMC 1.0 CA.3.162 Implementation:
If your company has developed any software internally and uses it internally it needs to undergo a security assessment. The assessment can be completed by your employees or by a third party.
CMMC 1.0 CA.3.162 Scenario(s):
- Scenario 1:
Your company has several developers. One of your developers built a piece of software for the accounting department to help automate some of their tasks. Because the software is internally developed and used internally it must under go a security assessments. You task one of your developers to use the OWASP Code Review guide to assess internally developed software.
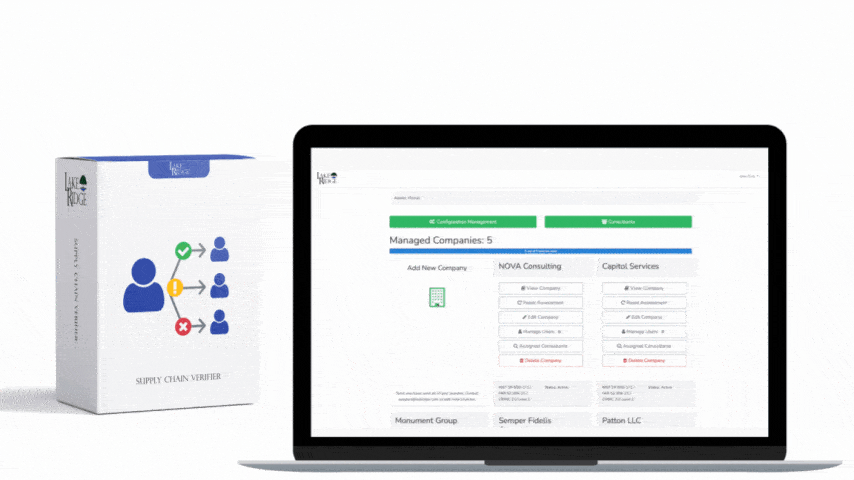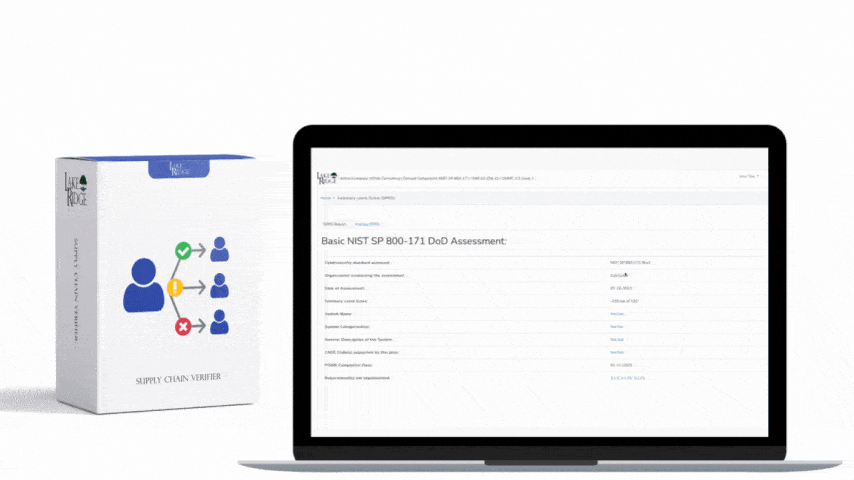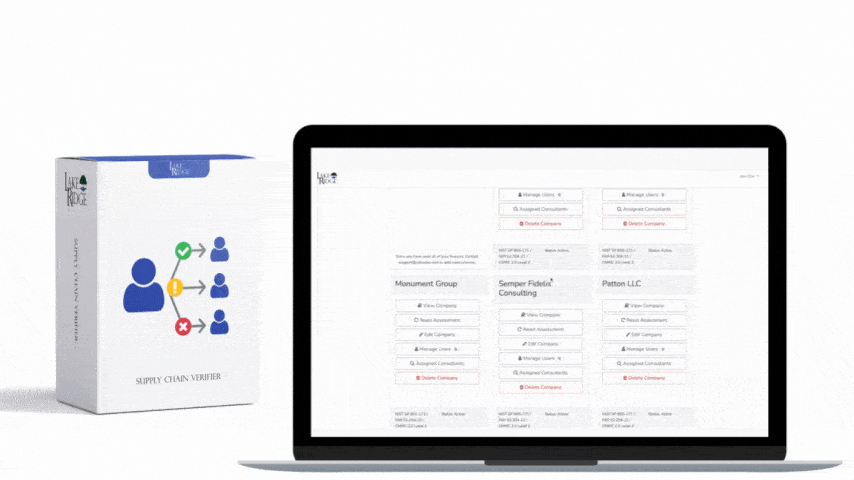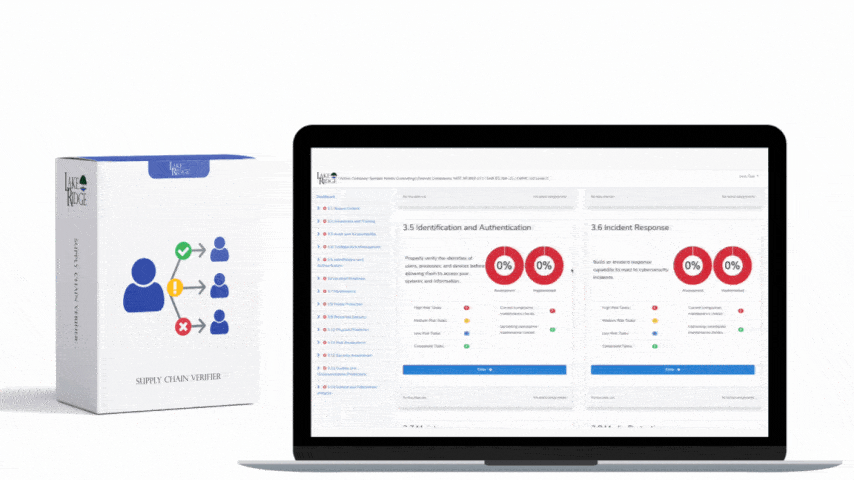
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you