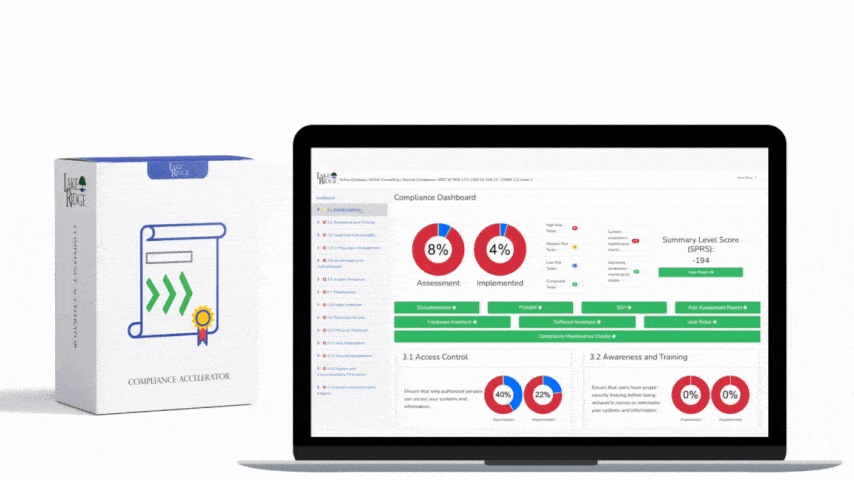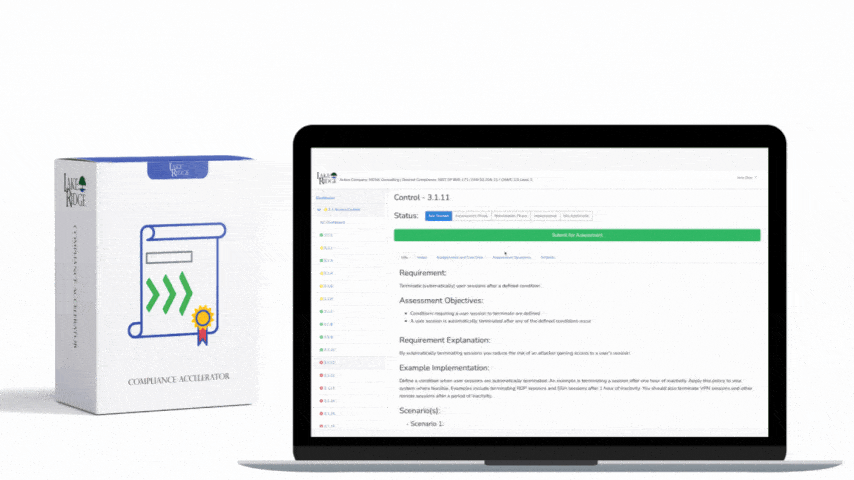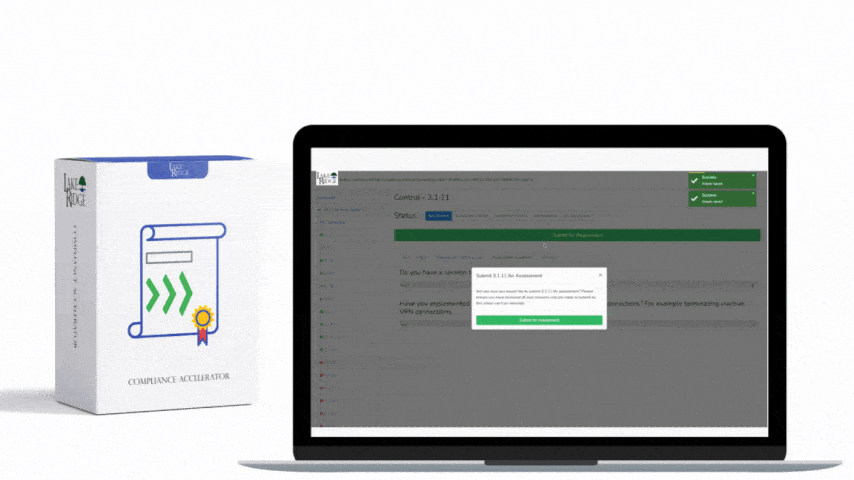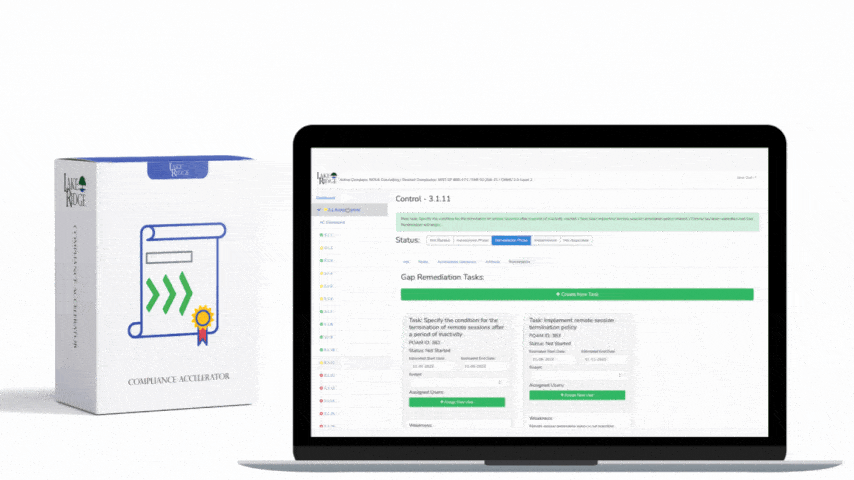
CMMC 1.0 Practice CM.2.064 Requirement:
Establish and enforce security configuration settings for information technology products employed in organizational systems
CMMC 1.0 CM.2.064 Requirement Explanation:
By default systems are insecure. By deploying DISA STIGs or CIS benchmarks to your systems you can increase their security. DISA STIGs are available for a wide range of devices and operating systems. They provide detailed guidance on how to harden your systems.
Example CMMC 1.0 CM.2.064 Implementation:
Implement security configuration settings on your systems using DISA security technical implementation guides (STIGs) or CIS Benchmarks. Apply security configuration settings to all your systems. This includes workstations, servers, network devices, and printers. Document the security configuration settings you have applied.
CMMC 1.0 CM.2.064 Scenario(s):
- Scenario 1:
You need to harden her company's Windows 10 workstations. To do this you locate the security technical implementation guides for Windows from the DISA website. You select the settings you wants to deploy and document them in the DISA STIG viewer app. You then apply the security settings to your workstations using group policy.
- Scenario 2:
You deployed DISA STIG configuration settings to your organization’s Windows 10 workstations. A developer complains that the changes have interfered with his dev environment on his computer. He is unable to complete his work. You identify the incompatible setting, document it. You then document a business justification for not applying it to developer laptops. Management approves the change and you remove the setting from his computer.
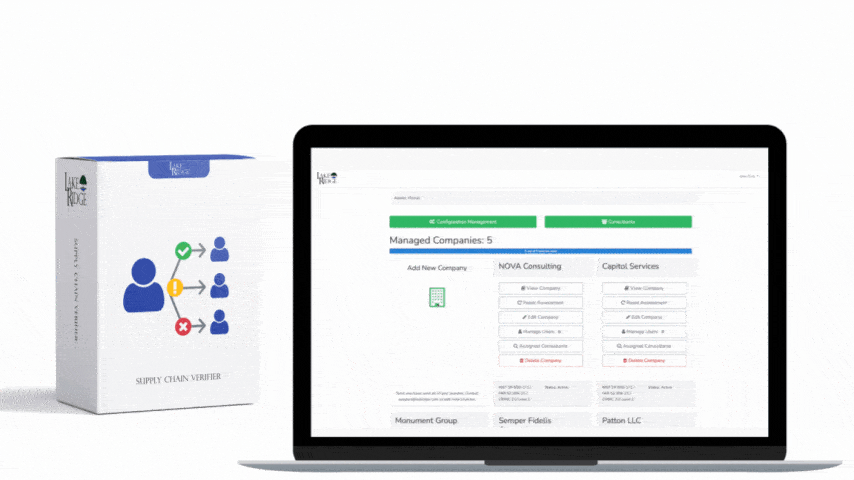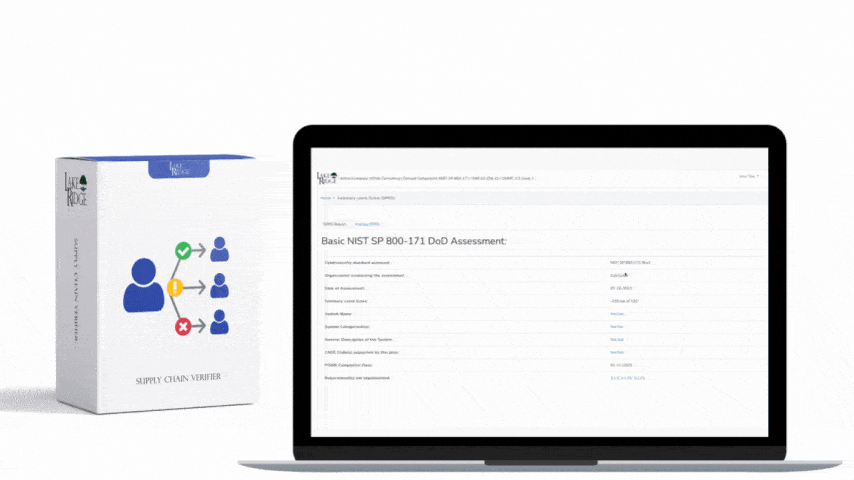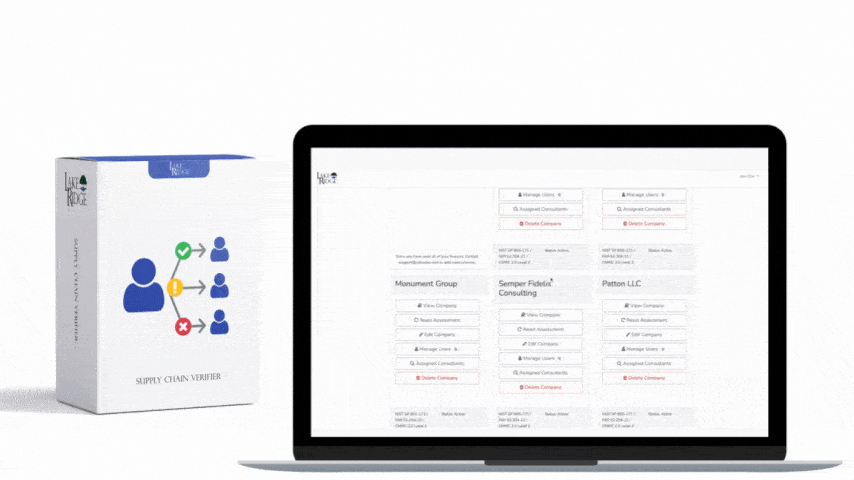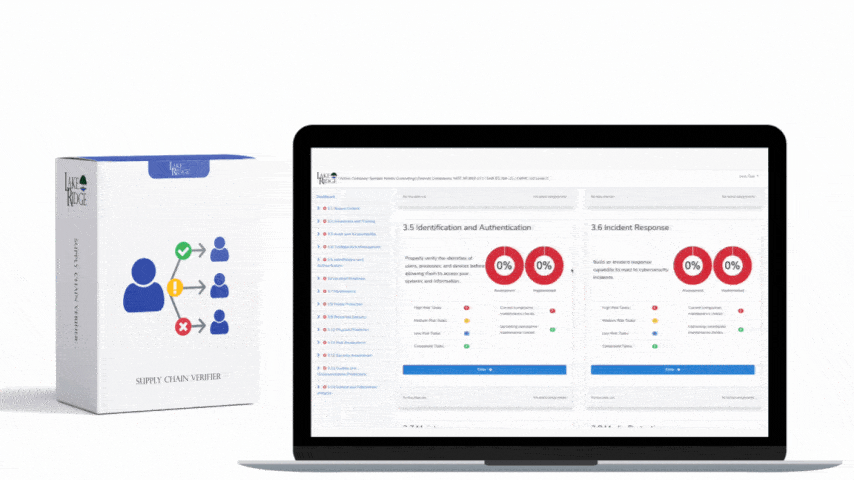
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you