CMMC 1.0 Practice SC.1.176 Requirement:
Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
CMMC 1.0 SC.1.176 Requirement Explanation:
The goal of a DMZ is to add an extra layer of security to your local area network.
Example CMMC 1.0 SC.1.176 Implementation:
Do not place servers or other IT systems that need to be accessible from the internet on to your local network. Instead, set up a "demilitarized zone" (DMZ). Place your systems that need to be accessed over the internet (e.g. web server) into your DMZ. Alternatively, you may move your systems that need to be publicly accessible to the cloud. Because you don't host anything that needs to be publicly accessible you would not need a DMZ.
CMMC 1.0 SC.1.176 Scenario(s):
- Scenario 1:
Alice has built a server that will host her company's website. Instead of insecurely placing the webserver on her internal network she creates a DMZ and places the webserver in it. The web server is now accessible from the internet and is separate from her company network. If a hacker takes over the webserver he gets trapped in the DMZ and can't access the internal network.
- Scenario 2:
Alice needs to find a solution to host her company's new website. Instead of setting up her own web server and DMZ, she decides to use a web hosting company. As a result, does she avoids having to set up a DMZ.
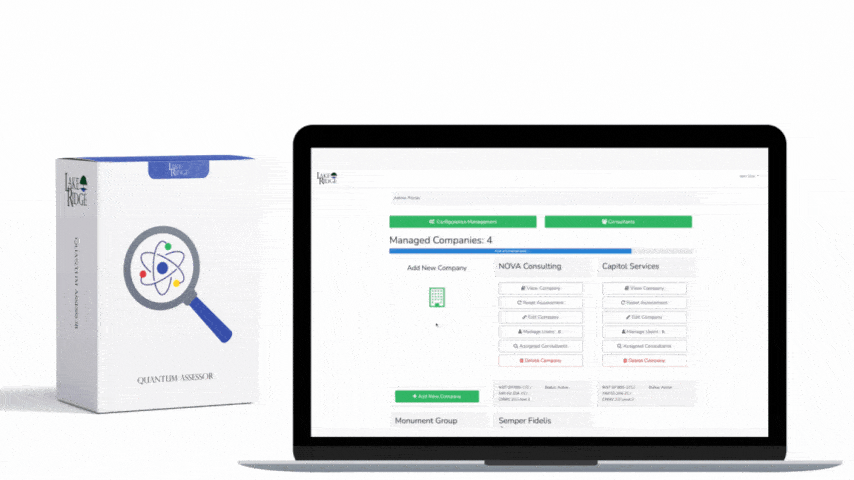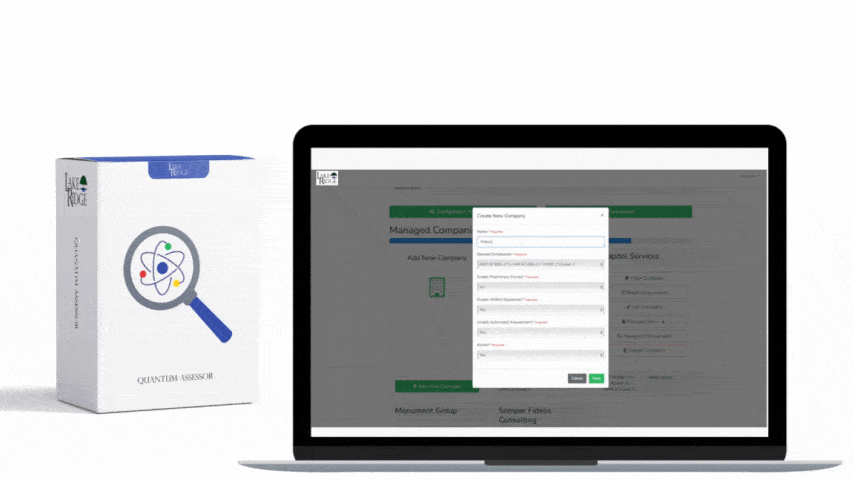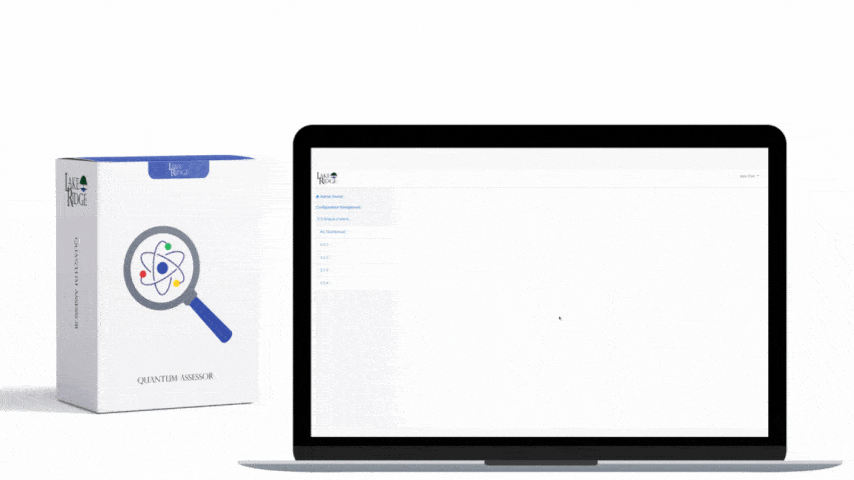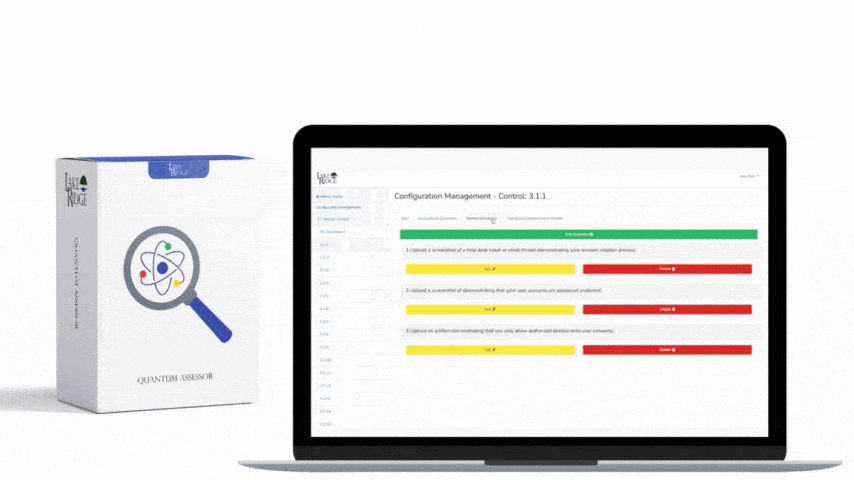
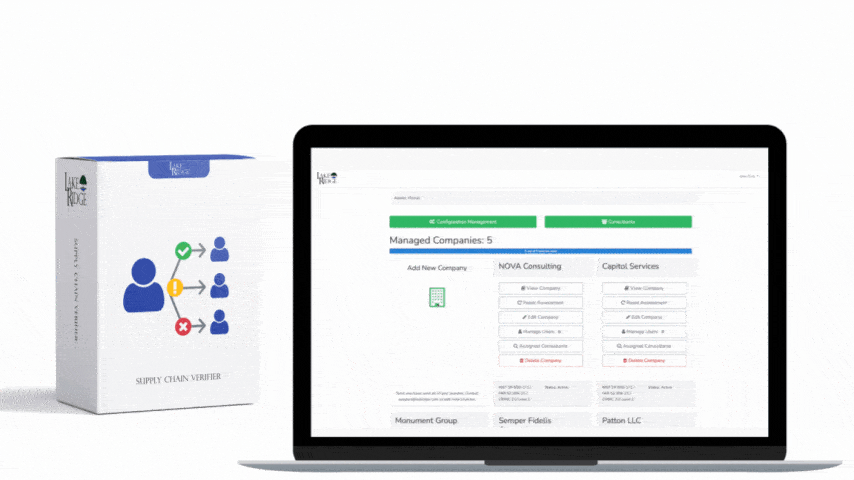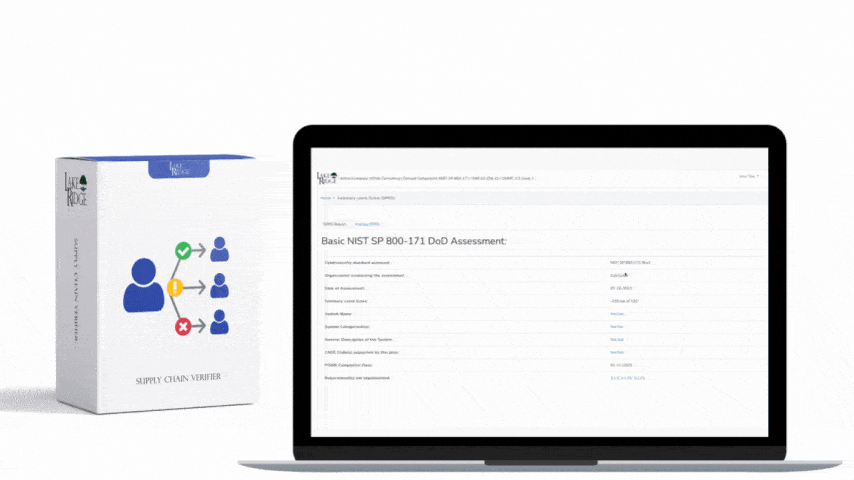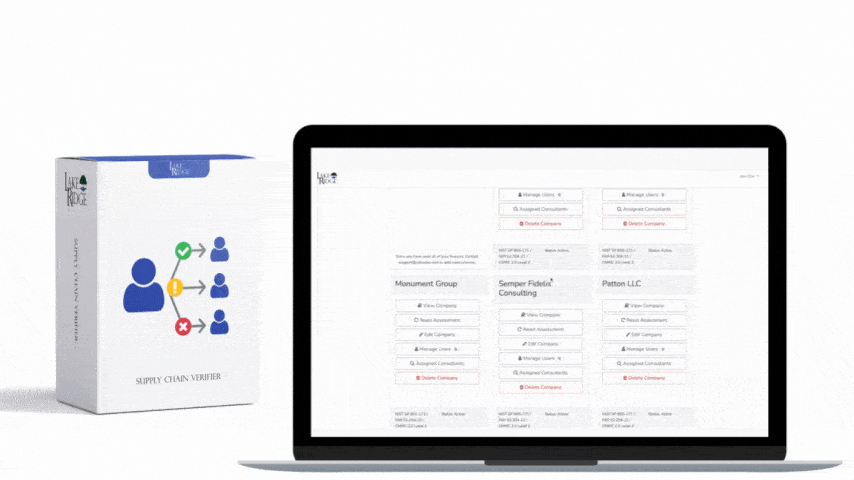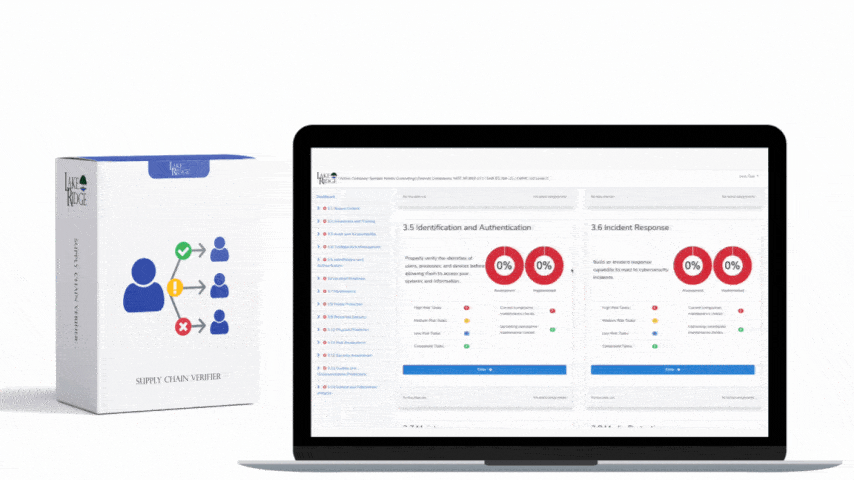
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you