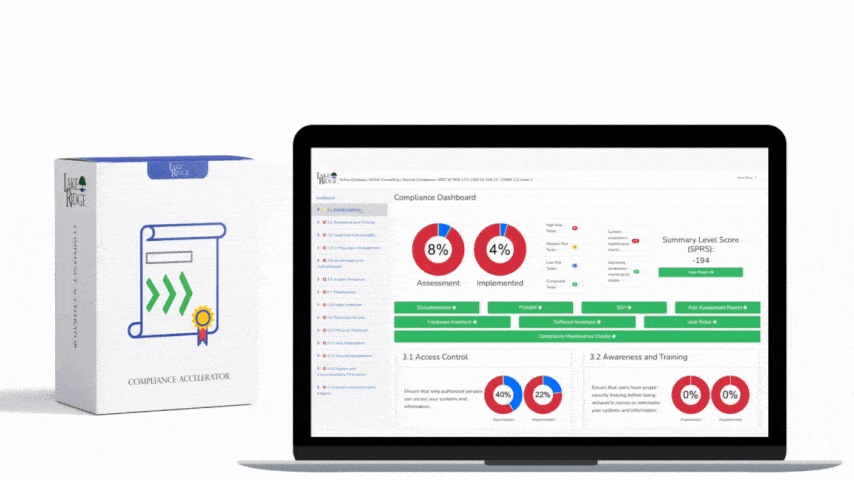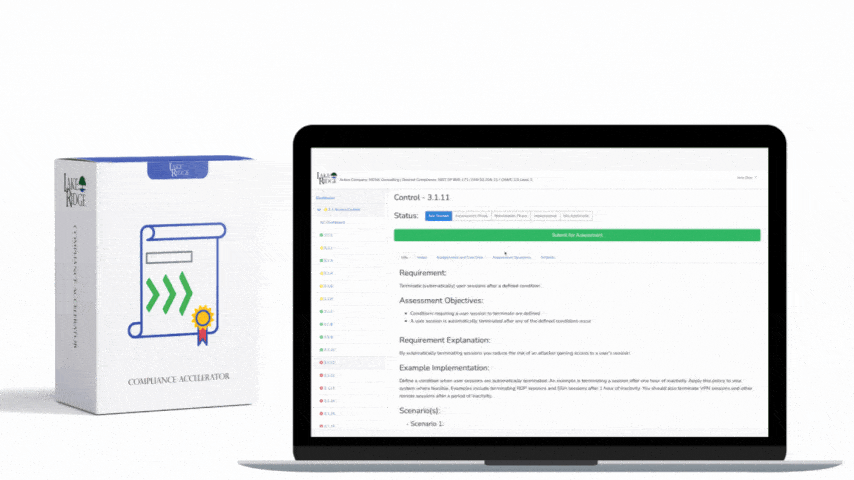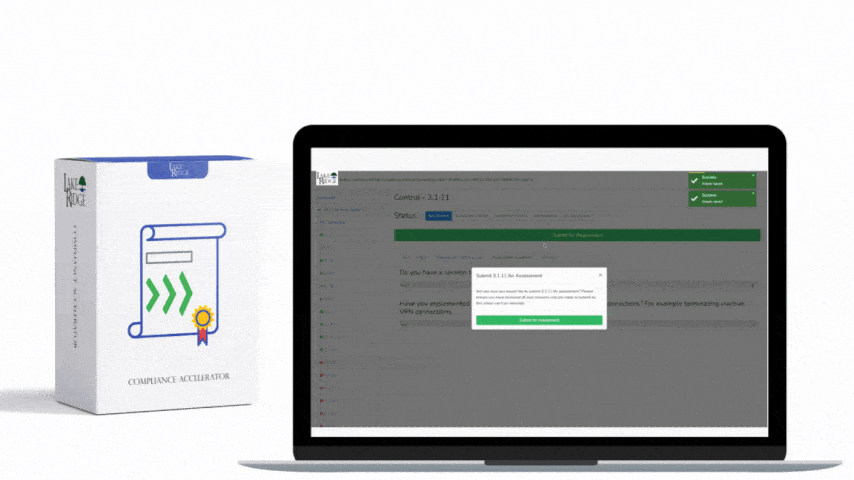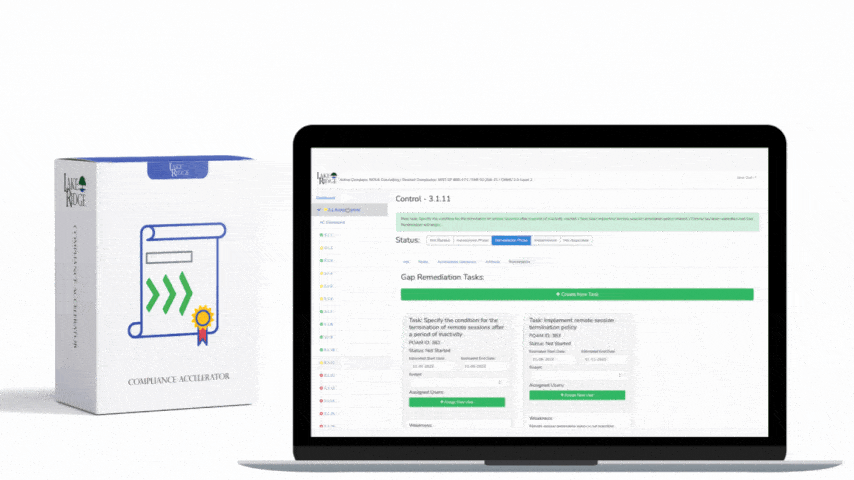
NIST SP 800-171 & CMMC 2.0 3.3.9 Requirement:
Limit management of audit logging functionality to a subset of privileged users.
NIST SP 800-171 & CMMC 2.0 3.3.9 Requirement Explanation:
System administrators have full control of their systems, this allows them to modify everything including audit logs. They can potentially delete logs indicating that they have violated a security policy. To avoid this you should not allow system administrators to control and carry out auditing tasks.
Example NIST SP 800-171 & CMMC 2.0 3.3.9 Implementation:
Separate system administration duties from audit logging management duties. Persons that are responsible for creating users, resetting passwords, installing software, and other admin tasks should not have access to your syslog server and SIEM.
NIST SP 800-171 & CMMC 2.0 3.3.9 Scenario(s):
- Scenario 1:
You are a small company and have one system administrator who manages all of your systems. You do not want him to be able to delete audit logs off of your syslog server or carry out audit activities using your SIEM. To accomplish this you do not provide him access to these systems. If you temporarily need his technical assistance on your syslog server or SIEM you provide him temporary access and supervise him while he completes his assigned task.
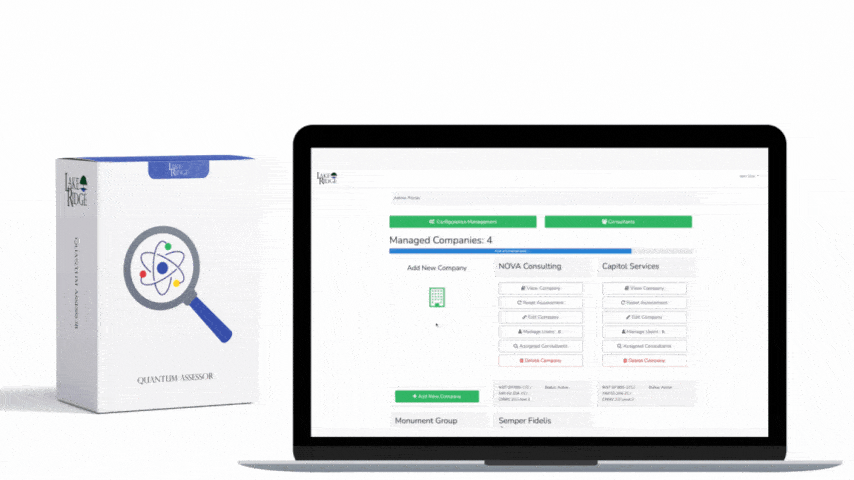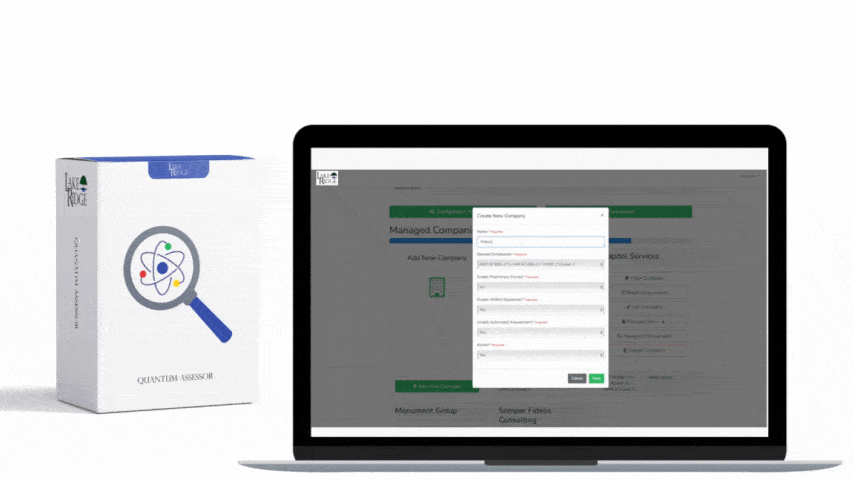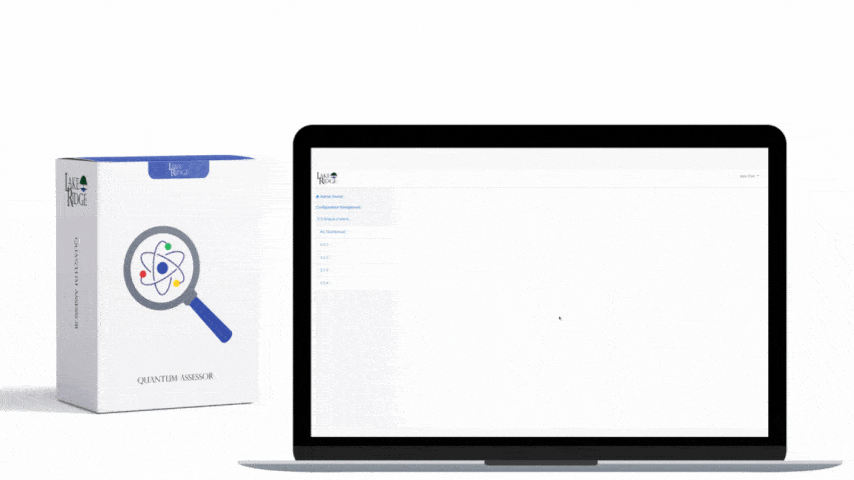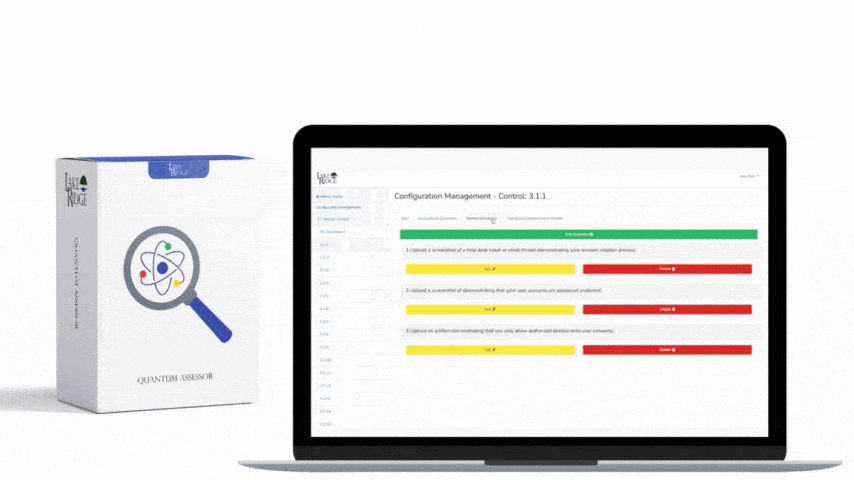
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you