CMMC 1.0 Practice AC.2.016 Requirement:
Control the flow of Federal Contract Information in accordance with approved authorizations.
CMMC 1.0 AC.2.016 Requirement Explanation:
By placing a firewall or other proxy between your network and the internet you prevent direct access to your systems from the internet. You can also prevent certain types of information from exiting your network.
Example CMMC 1.0 AC.2.016 Implementation:
Use a firewall to control traffic coming in and out of your network. Configure the firewall to only allowed authorized connections out of your network. Use the firewall or proxy device to ensure that sensitive information is only allowed to exit your network if encrypted.
CMMC 1.0 AC.2.016 Scenario(s):
- Scenario 1:
You setup a firewall on your network. This prevents traffic from flowing directly from your internal network to the internet. Your firewall analyzes traffic and only allows authorized traffic through.
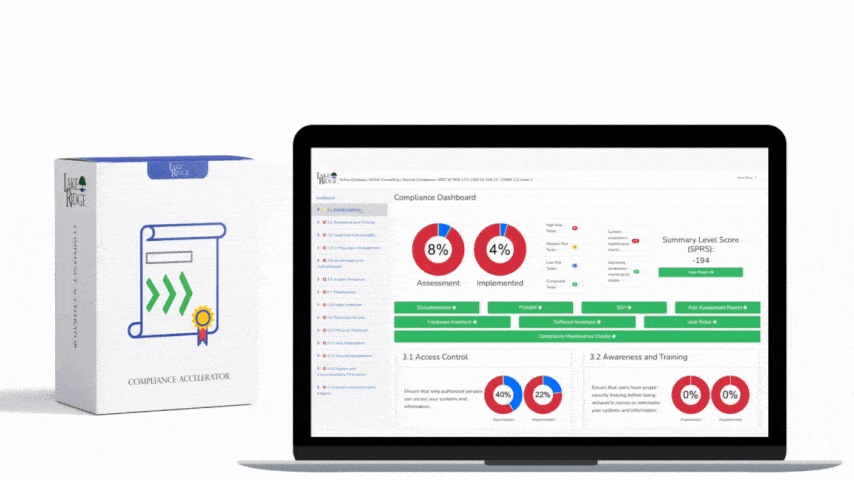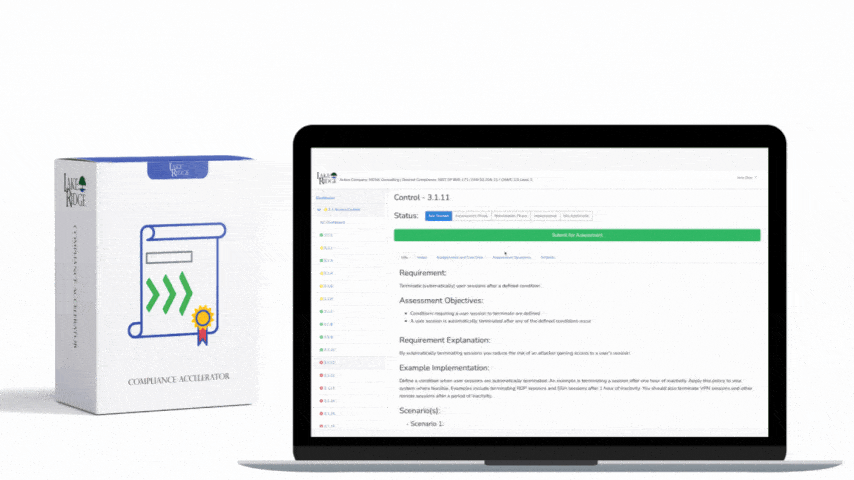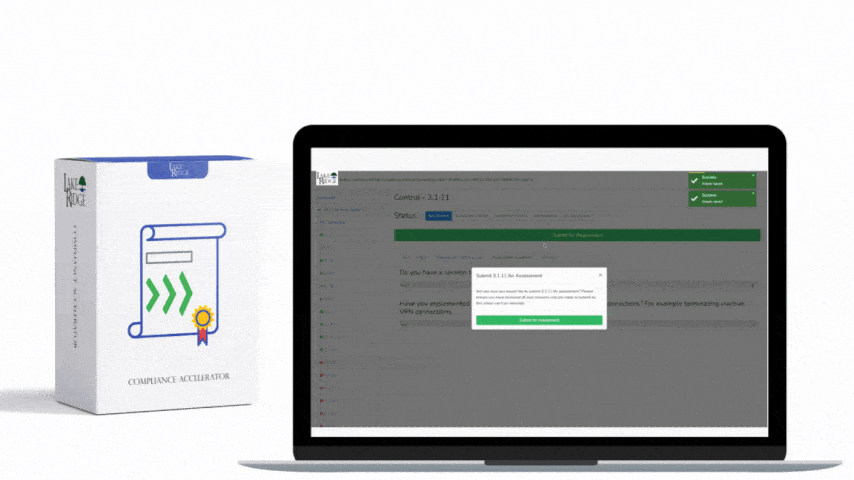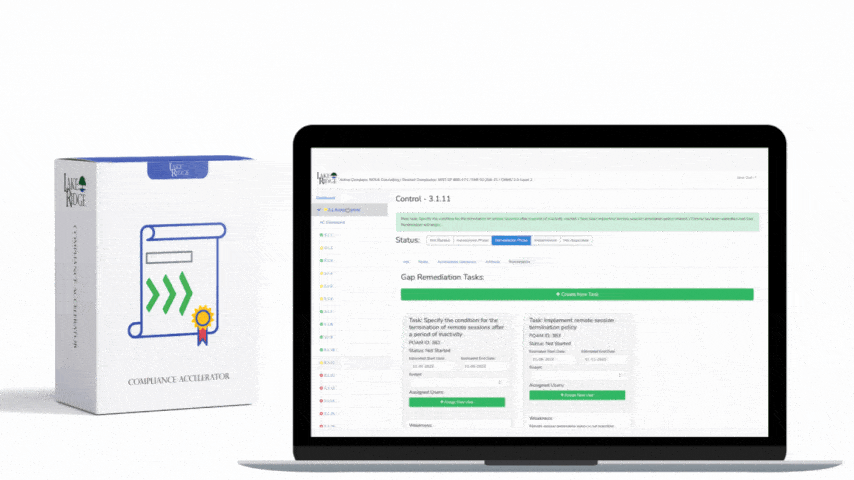
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you