Security is in our DNA
Lake Ridge Application & Corporate Security

Where are Lake Ridge Apps Hosted?
Lake Ridge Apps are hosted on Amazon Web Services (AWS) East. “AWS US East has been granted a Joint Authorization Board Provisional Authority-To- Operate (JAB P-ATO) and multiple Agency Authorizations (A-ATO) for moderate impact level.” Amazon continually manages risk and undergoes recurring assessments to ensure compliance with industry standards. Amazon’s data center operations have been accredited under: ISO 27001, SOC 1 and SOC 2/SSAE 16/ISAE 3402 (Previously SAS 70 Type II), PCI Level 1, FISMA Moderate, and Sarbanes-Oxley (SOX).
Application Encryption
All encryption modules used by Lake Ridge applications are FIPS compliant. All data processed, stored, and transmitted by Lake Ridge applications is encrypted in transit and at rest using Federal Information Processing Standards (FIPS) compliant algorithms. All data in transit is protected using AES 256 and SHA-256 algorithms. All data at rest is encrypted using AES 256 bit encryption.
Who Can See My Application Data?
Lake Ridge account passwords are hashed using AES 256 bit encryption. Our own staff can't even view them. If you lose your password, it can't be retrieved—it must be reset. Only Lake Ridge technical staff with a need-to-know can see your data such as responses to assessment questions, file uploads, and other information you enter into Lake Ridge applications. Lake Ridge adheres to the NIST SP 800-17 requirements surrounding separation of duties and providing access to resources on a need-to-know basis.
Development Practices & Application Security
We develop following security best practices and frameworks (OWASP Top 10, SANS Top 25). Lake Ridge apps are developed and version controlled using git. In addition to automated code coverage tests, and third-party automated security audits, all code is manually tested and reviewed for bugs and security vulnerabilities prior to deployment to production and staging environments. All databases are kept separate and dedicated to preventing corruption and overlap. Our certified security staff perform penetration tests against Lake Ridge applications.
How Are Application Logins Protected?
Logins to Lake Ridge apps are protected with Multi-Factor authentication. Passwords must be at least 10 characters in length and meet established complexity requirements. All login pages on our applications pass data via TLS 1.2+. We will suspend accounts for signs of irregular or suspicious login activity. We provide the capability to provide user accounts with varying levels of access. We have multiple layers of logic that segregate user accounts from each other.
Application Backups
Our servers store incremental backups so we can roll back to the exact second up to 4 days prior. Additionally we make a full daily backup of each database and test restores on a bi-weekly basis. Our backups are stored in Amazon data centers. Amazon’s data center operations have been accredited under: ISO 27001, SOC 1 and SOC 2/SSAE 16/ISAE 3402 (Previously SAS 70 Type II), PCI Level 1, FISMA Moderate, and Sarbanes-Oxley (SOX).
What Happens to My Data If I Unsubscribe?
All of the data you entered into the Lake Ridge application will be deleted from our databases within one year of you terminating your subscription.
Application Maintenance
Lake Ridge has established a window for planned maintenance outside of regular U.S. business hours. Regular business hours are defined between 9:00 AM and 5:00 PM United States Eastern time, Monday through Friday excluding U.S. Federal Holidays. In the event that unplanned maintenance is required, Lake Ridge will reach out to its customers.
Internal IT Security
Lake Ridge adheres to NIST SP 800-171 security practices and maintains a system security plan along with a plan of action and milestones document. NIST SP 800-171 includes 110 security practices that encompass important cybersecurity requirements such as access control, incident response, audit logging, and risk management.
Internal Protocol and Education
Employees are trained on best security practices, including how to identify social engineering, phishing scams, and hackers. Employees on teams that have access to customer data (such as tech support and our engineers) undergo criminal background checks prior to employment. All employees sign an acceptable use and privacy agreement.
Responsible Disclosure
If you’ve discovered a vulnerability in a Lake Ridge application, please don’t share it publicly. Instead, to report a security or privacy vulnerability, please send an email to security@lakeridge.io that includes: the specific product or service which you believe are affected, a description of the behavior you observed as well as the behavior that you expected, a numbered list of steps required to reproduce the issue and a video demonstration, if the steps may be hard to follow.
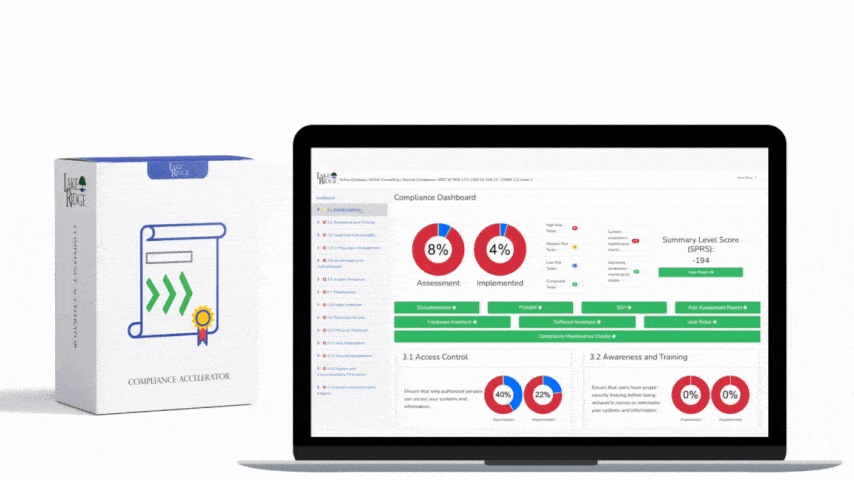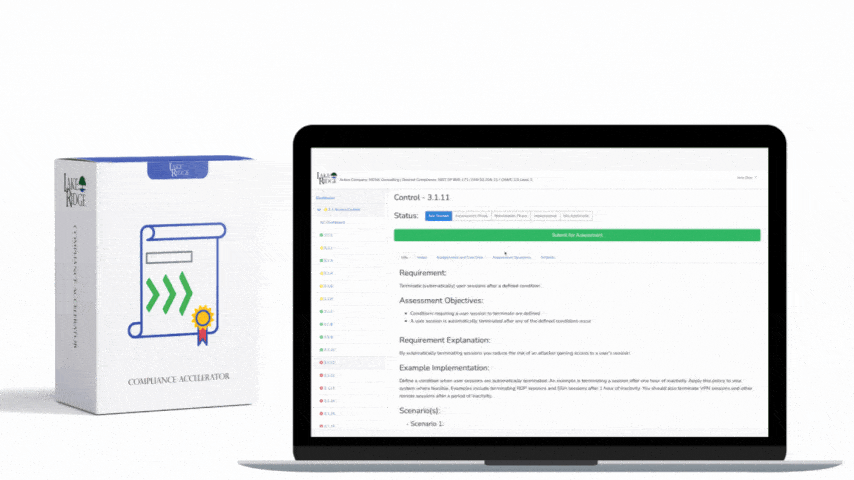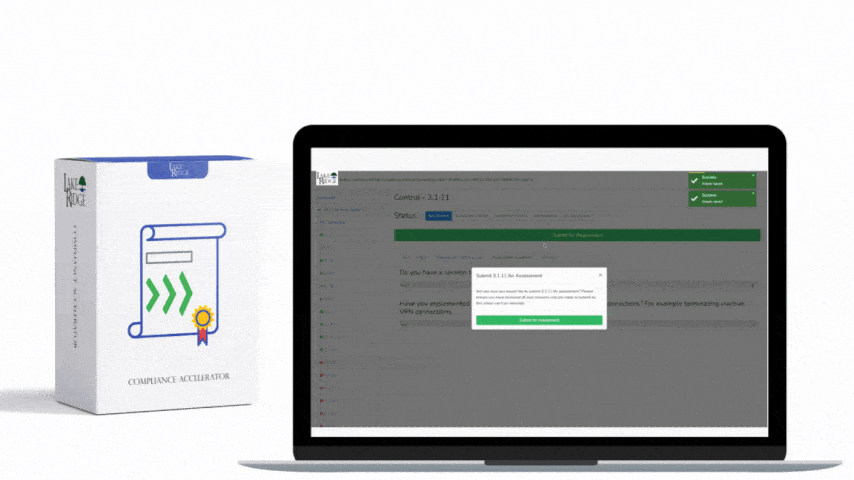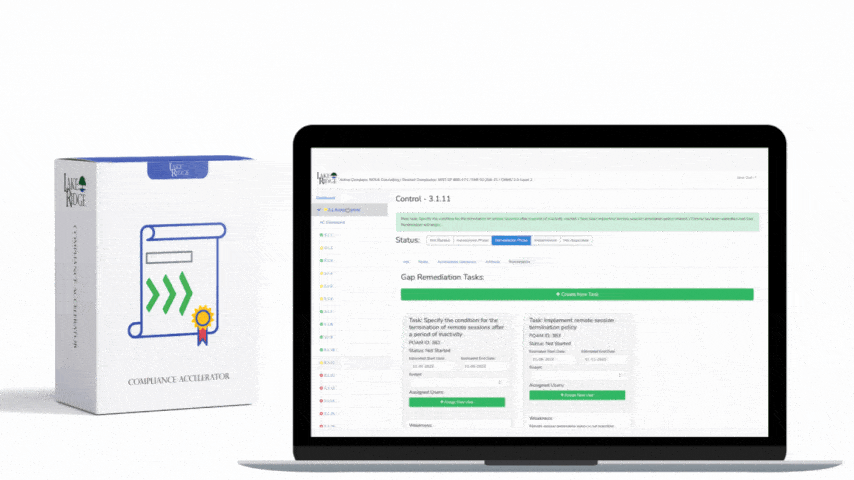
Quick & Simple
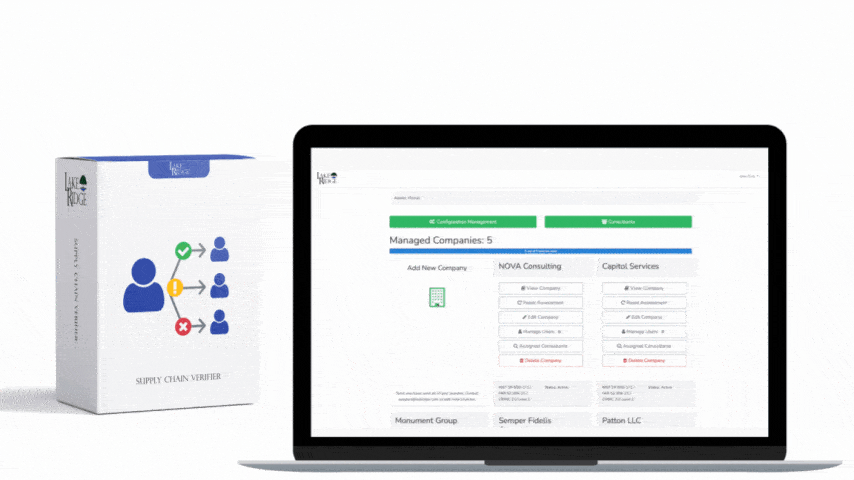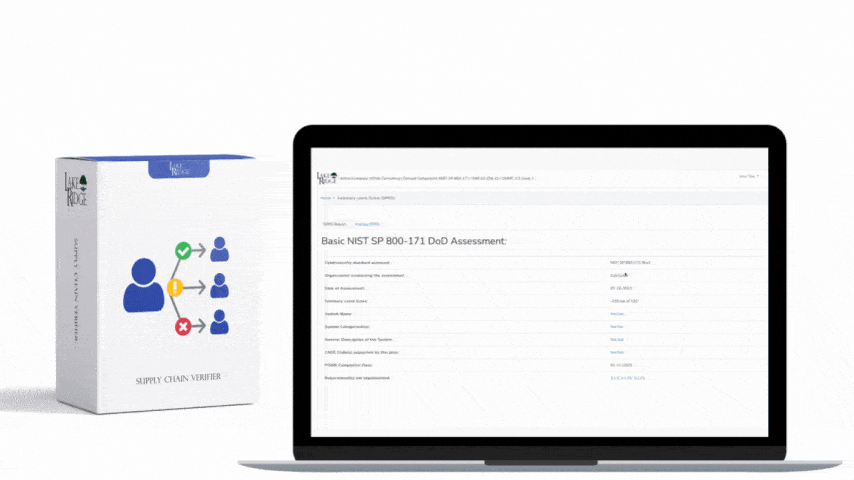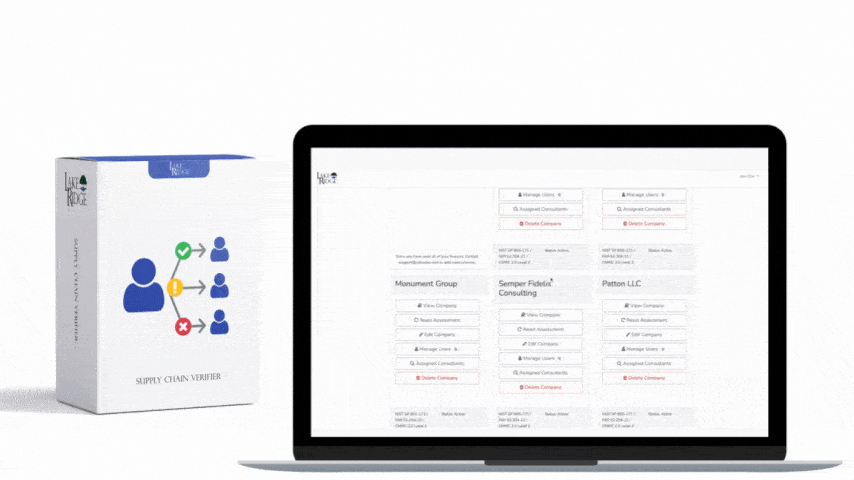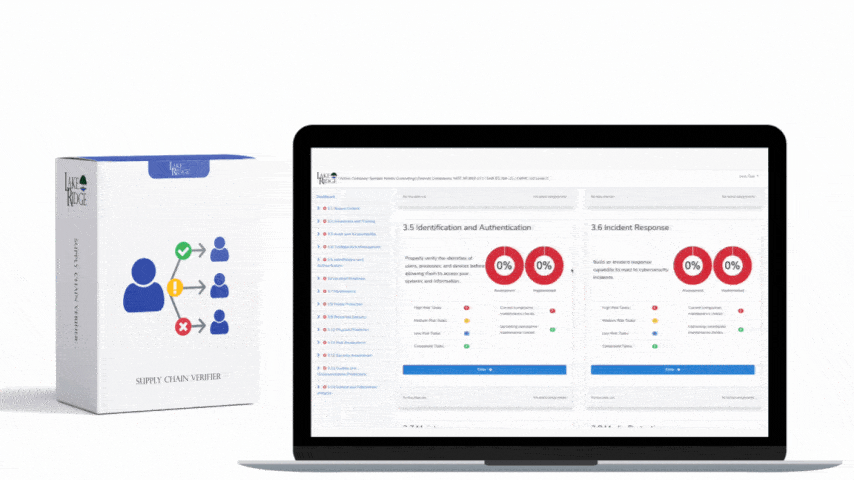
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you