CMMC 1.0 Practice RM.2.142 Requirement:
Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
CMMC 1.0 RM.2.142 Requirement Explanation:
By using a vulnerability scanner like Nessus you can quicklu identify vulnerabilities on your systems. Vulnerabilities often include outdated software and vulnerable default settings.
Example CMMC 1.0 RM.2.142 Implementation:
Use a vulnerability scanner to periodically (e.g. bi-weekly) scan systems on your internal and external network.
CMMC 1.0 RM.2.142 Scenario(s):
- Scenario 1:
You have purchased a vulnerability scanner to identify vulnerabilities in your systems. You configure it to scan everything on your network once a month. You also configure your scanner to updates its signature database before each scan. You document the results of your scans so that you can plan on mitigating the findings.
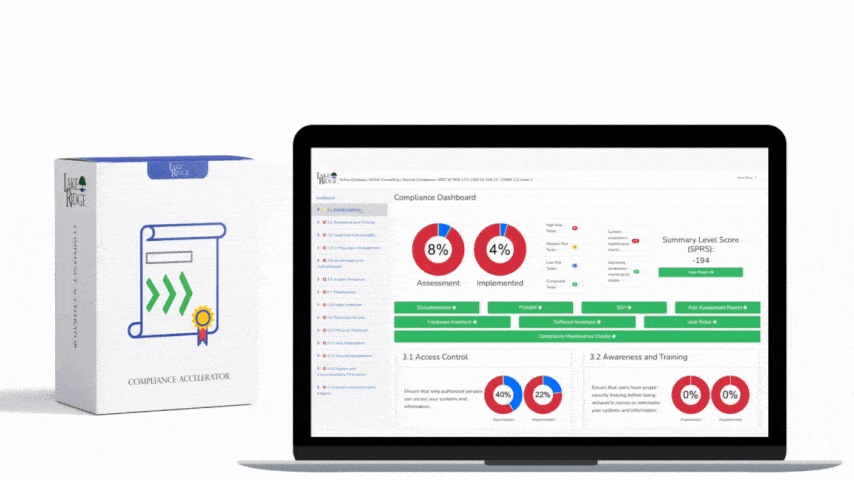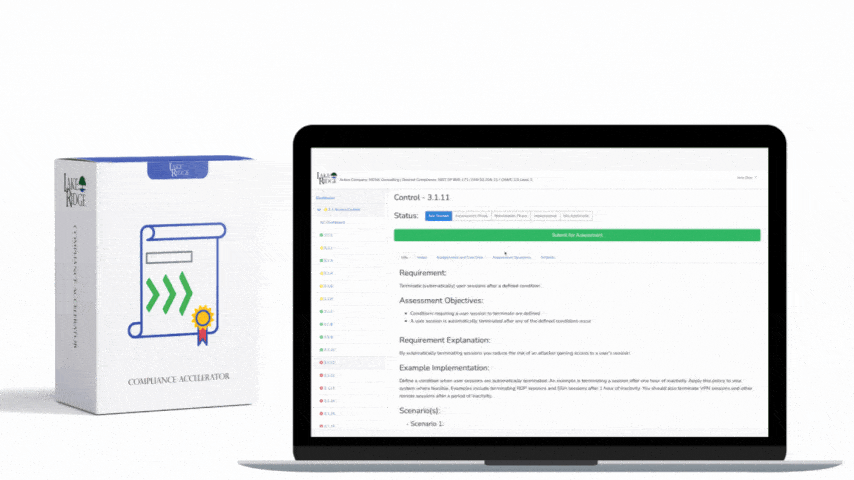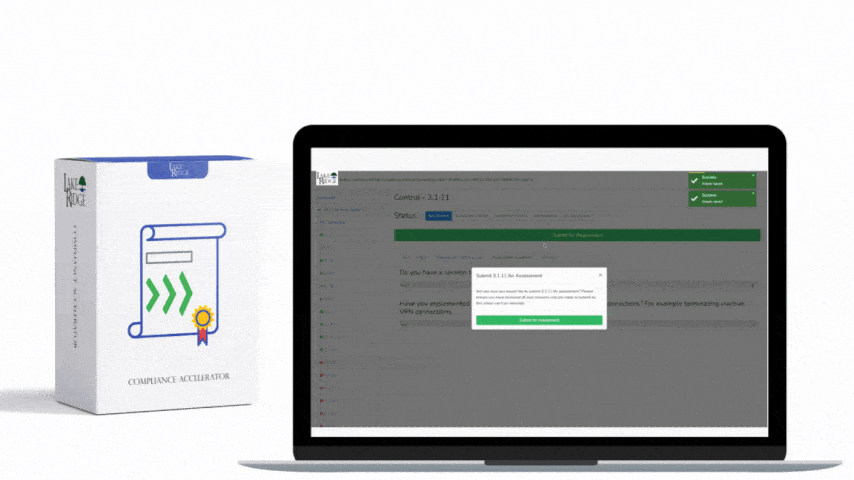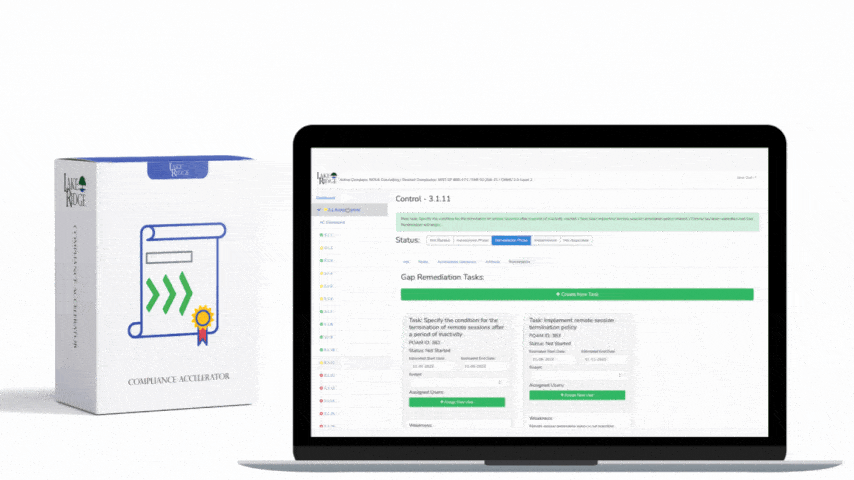
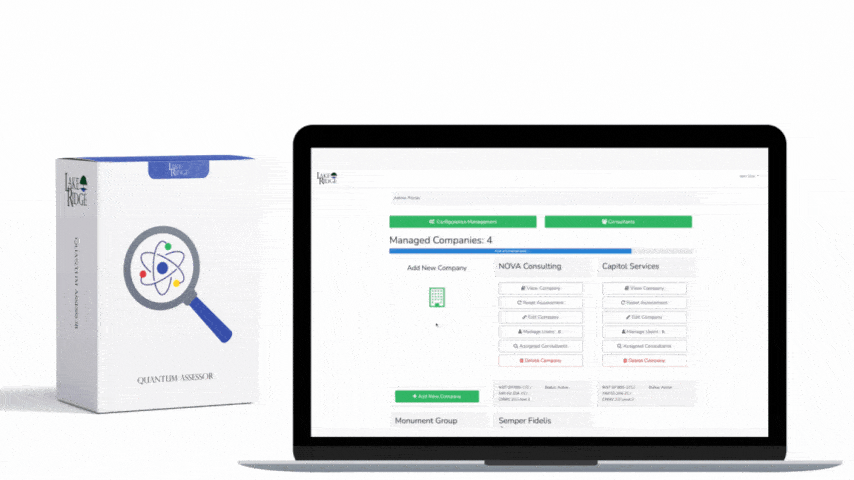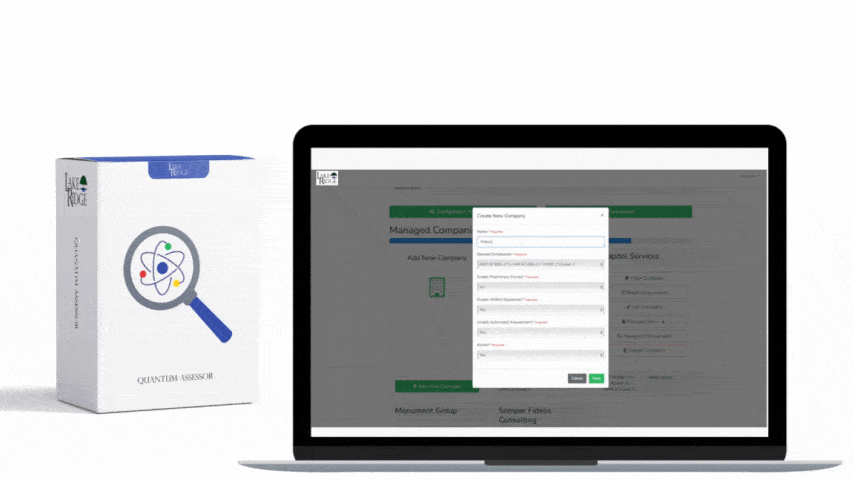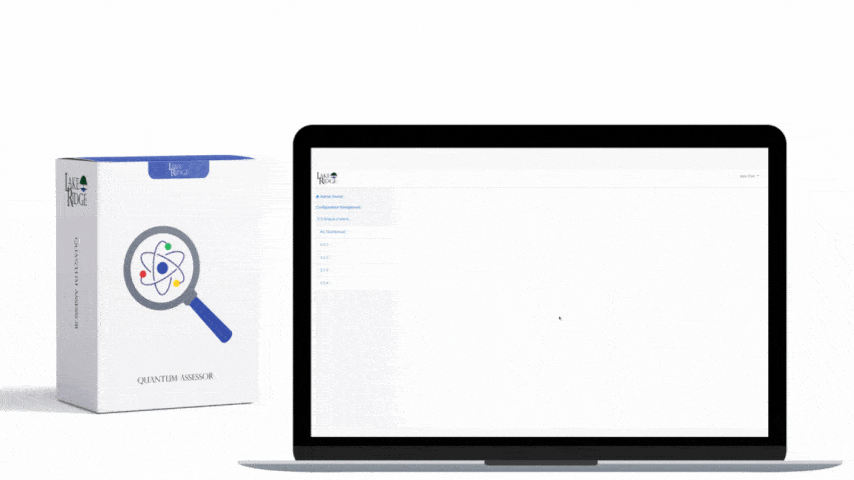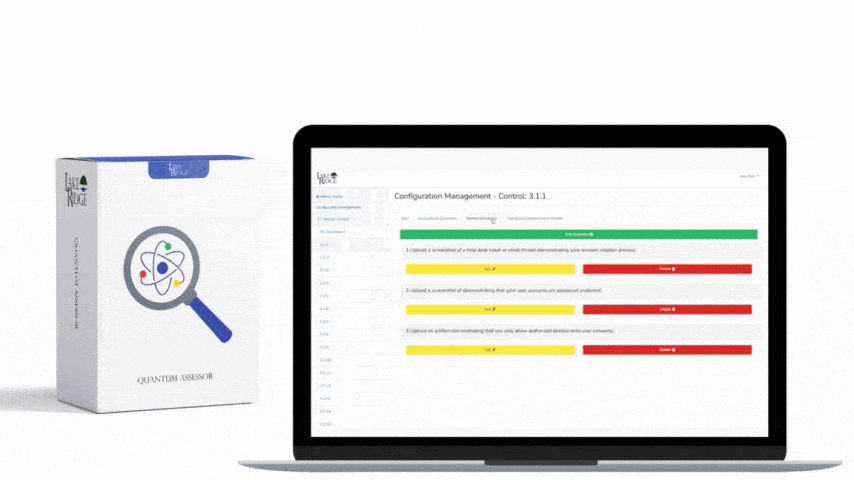
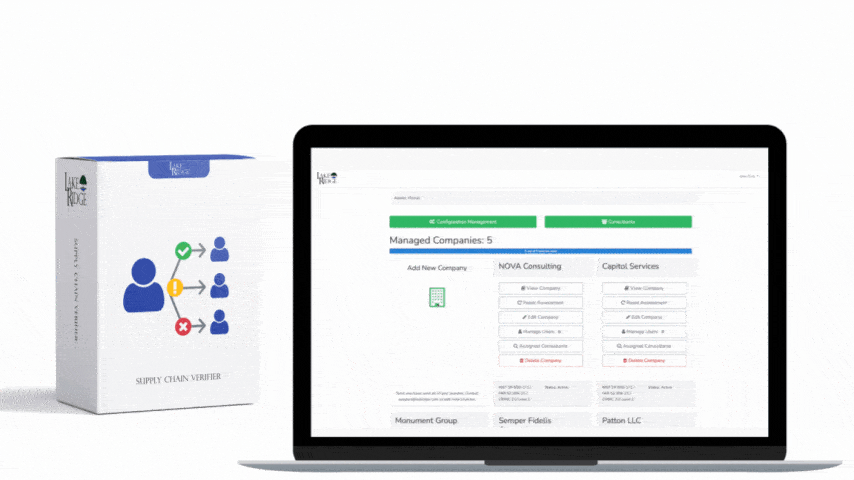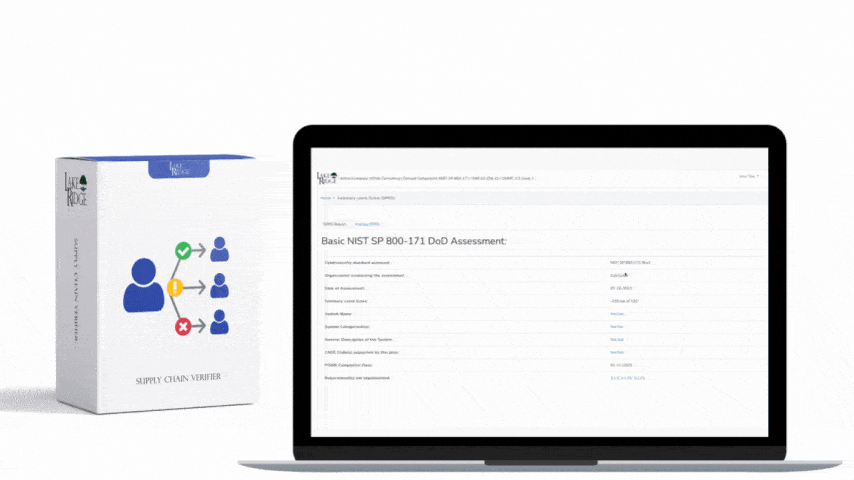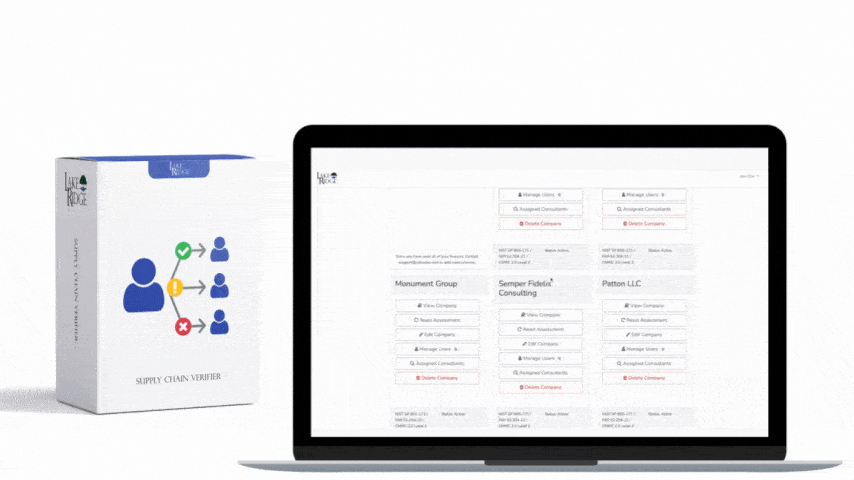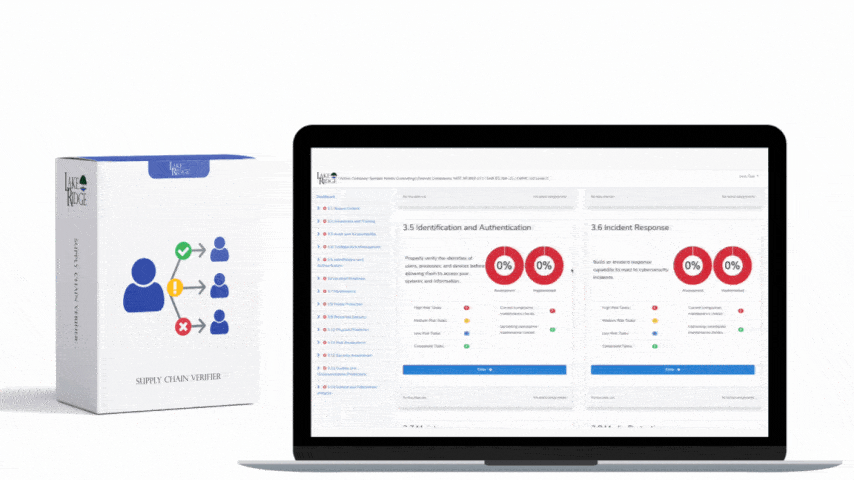
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you