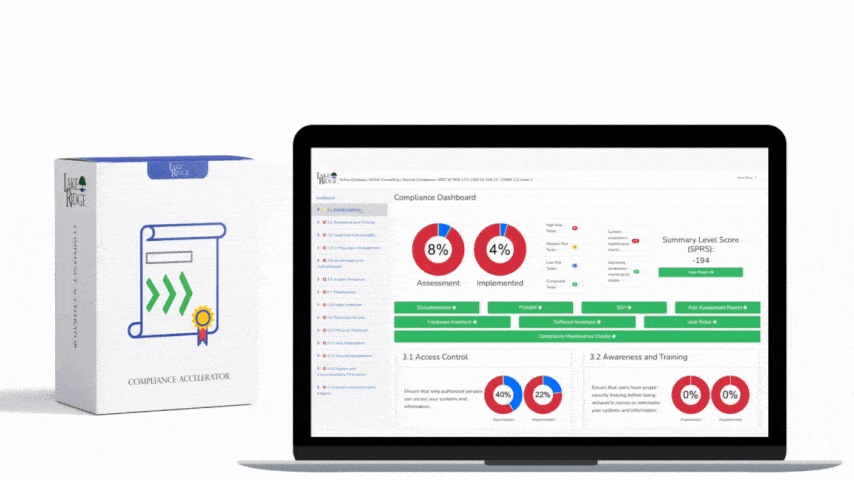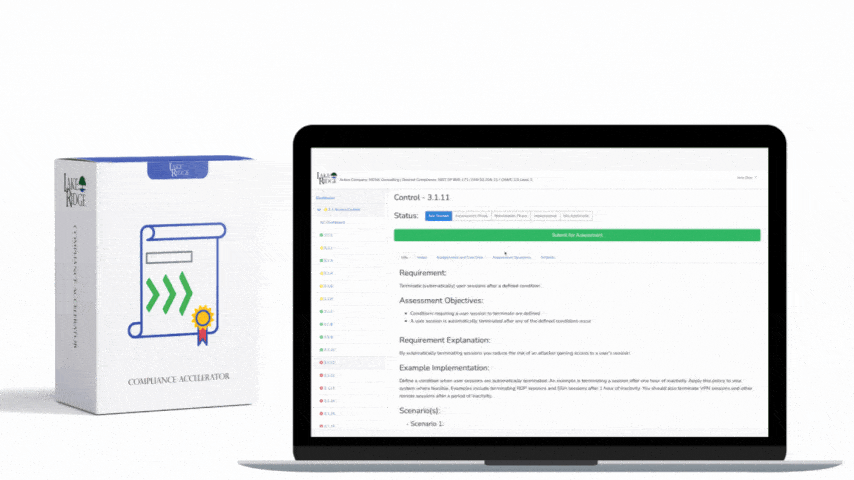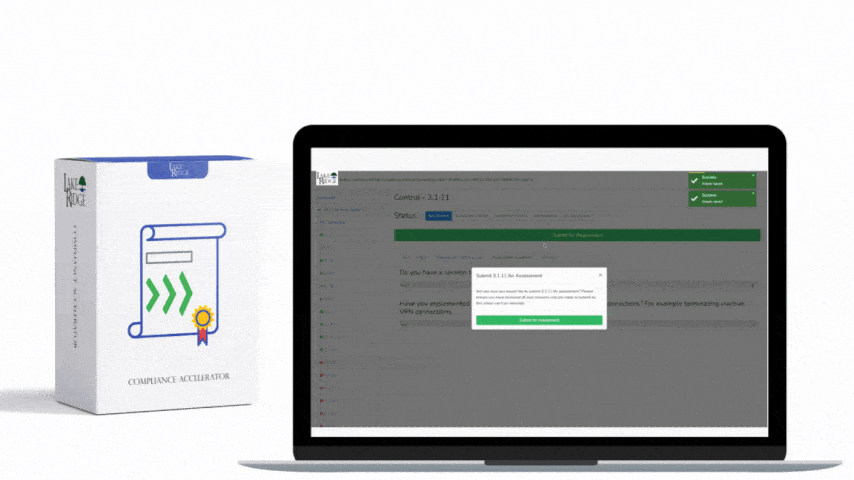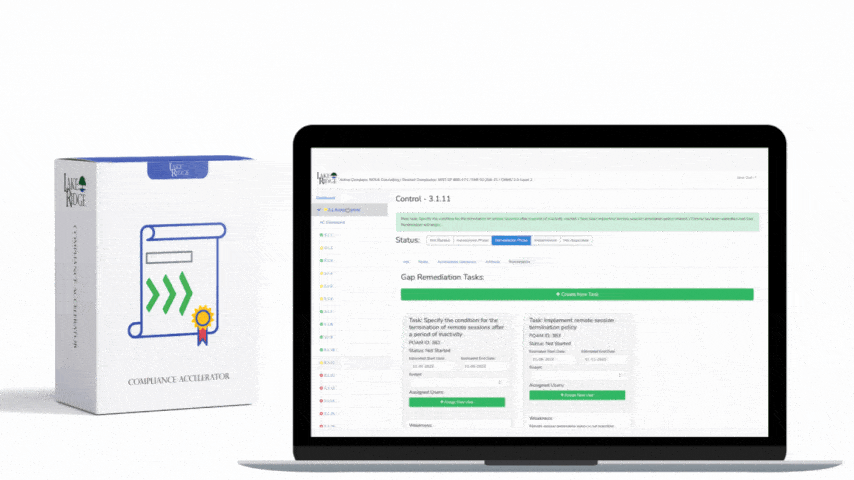
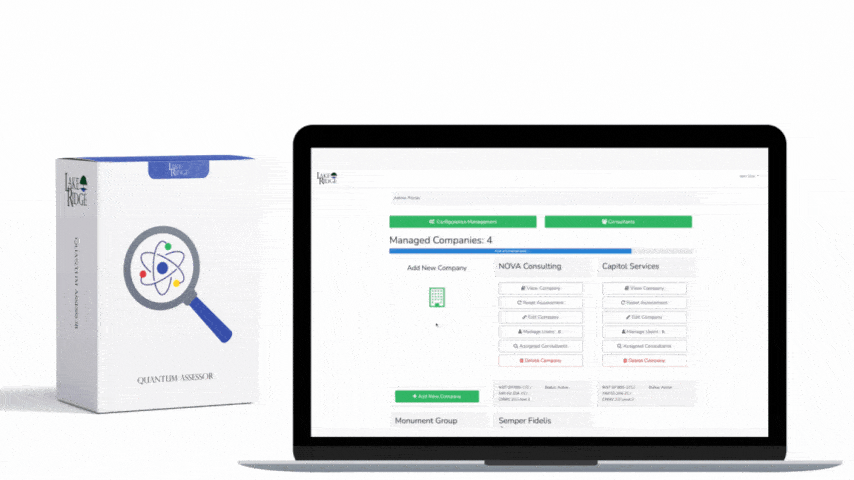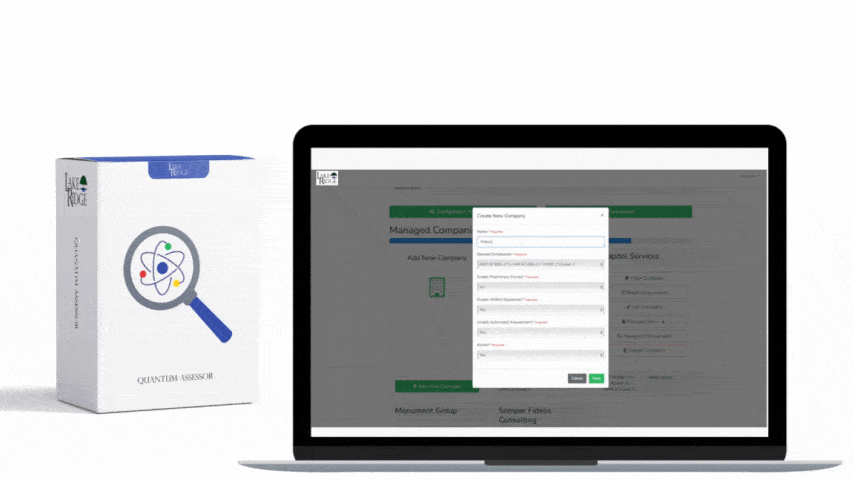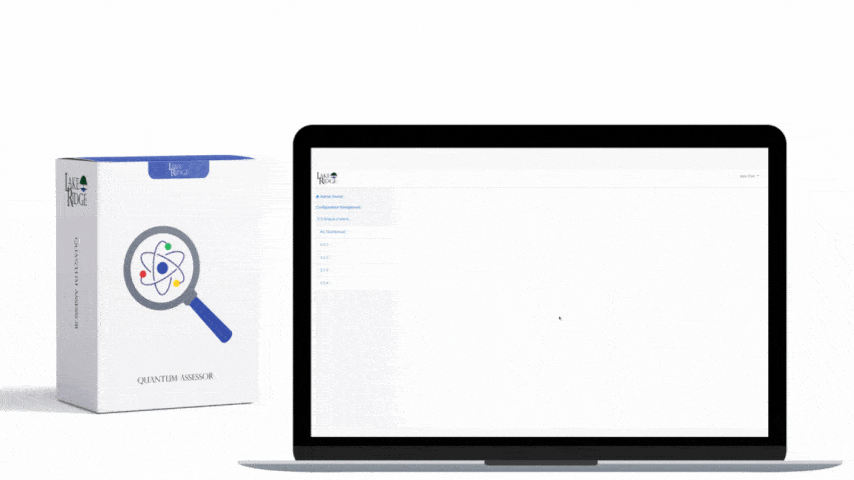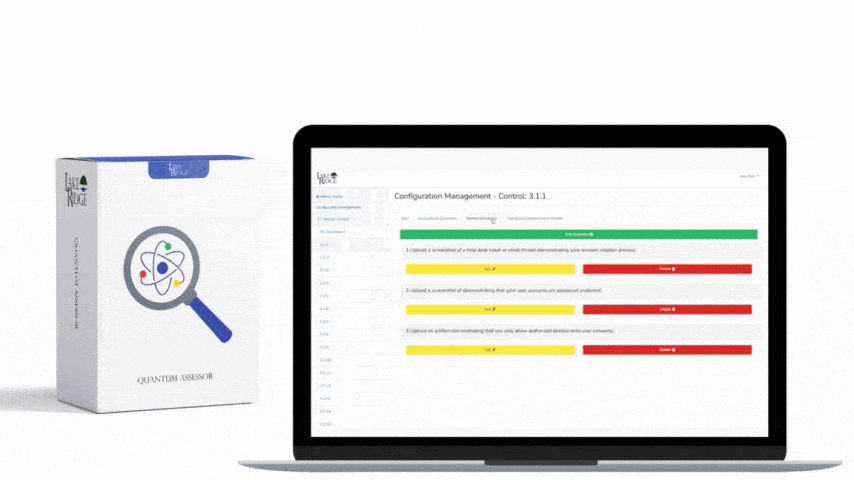
CMMC 1.0 Practice RM.2.143 Requirement:
Remediate vulnerabilities in accordance with risk assessments.
CMMC 1.0 RM.2.143 Requirement Explanation:
As far as this CMMC practice is concerned, risk assessments refer to the results of your vulnerability scans.
Example CMMC 1.0 RM.2.143 Implementation:
Remediate the vulnerabilities identified by your vulnerability scans. This often includes apply security updates and patches to your systems. Document the discovered vulnerabilities in a plan of action and milestones document so that you can track your progress towards mitigating them. Prioritize remediation in accordance with risk posed by the vulnerability.
CMMC 1.0 RM.2.143 Scenario(s):
- Scenario 1:
You conducted a vulnerability scan of your network and identified several vulnerabilities. The vulnerability scanner automatically categorizes them based on their level of risk. You add these vulnerabilities to your plan of action and milestone POA&M document and assign employees to mitigate them along with a due date. Once the vulnerabilities are mitigated you check them off your POA&M document.
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you