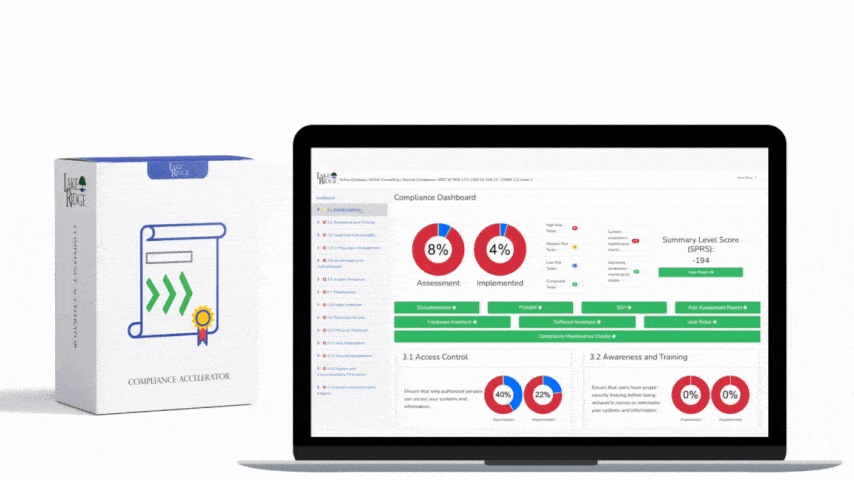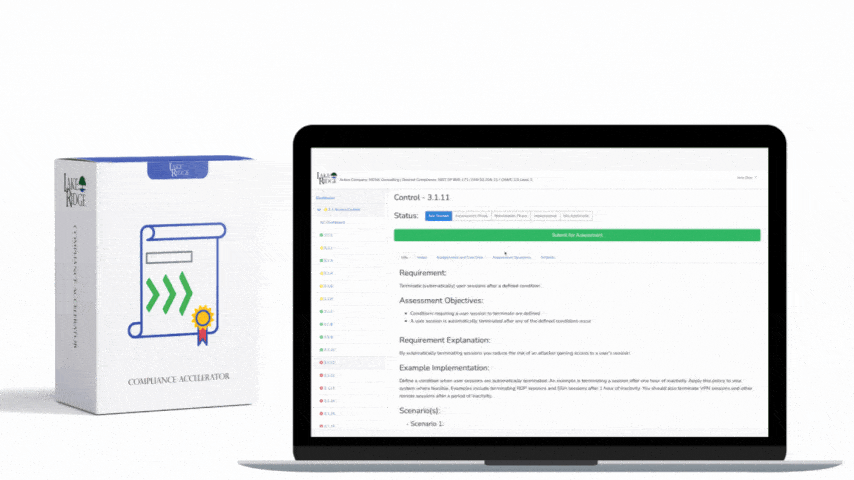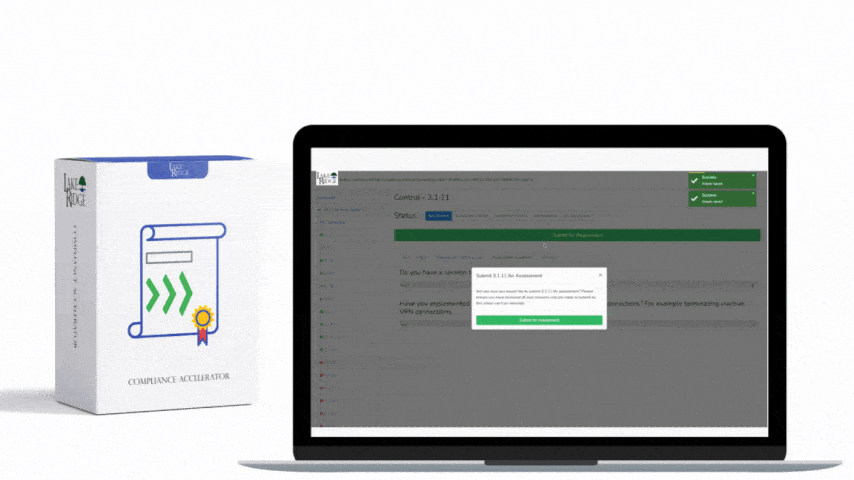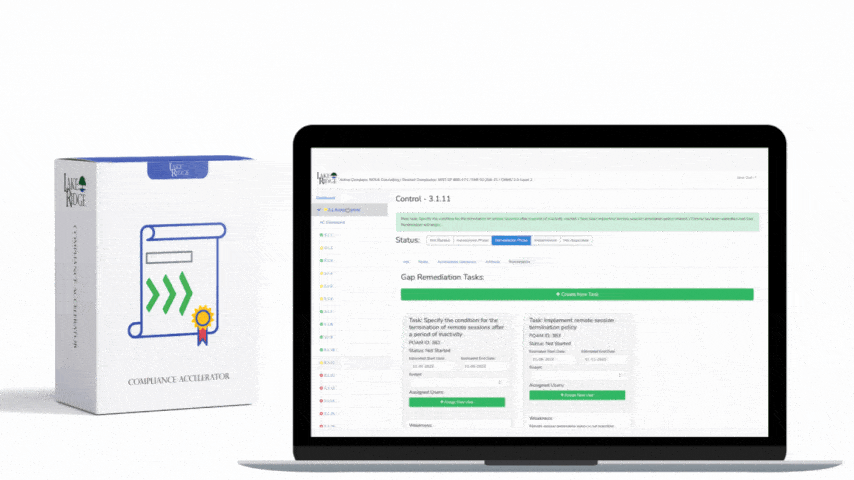
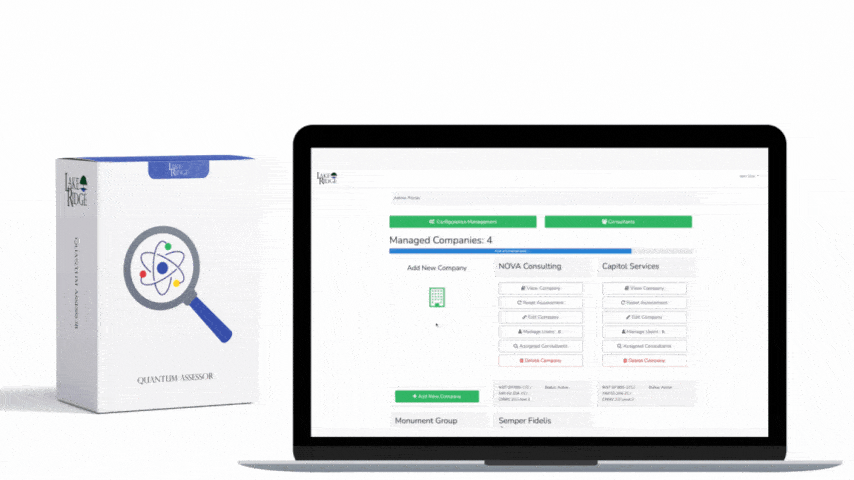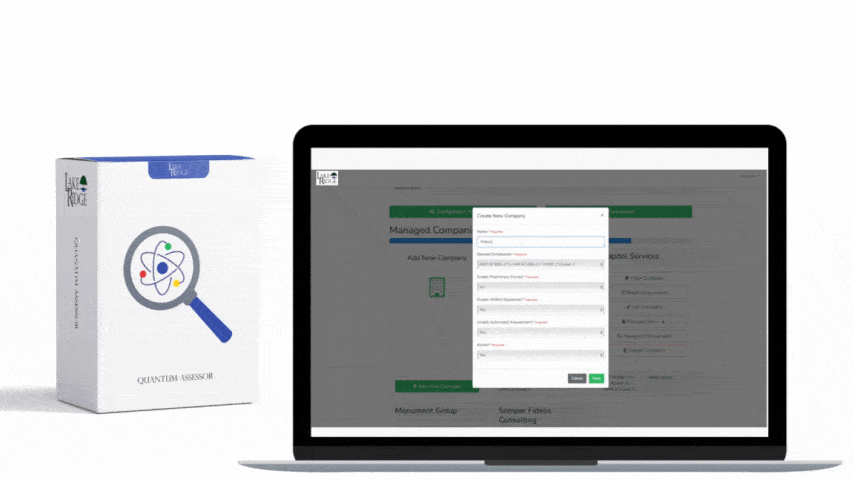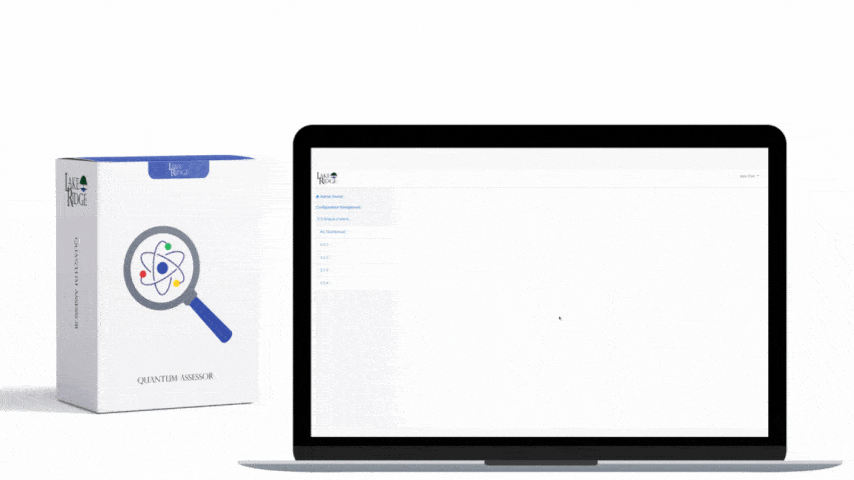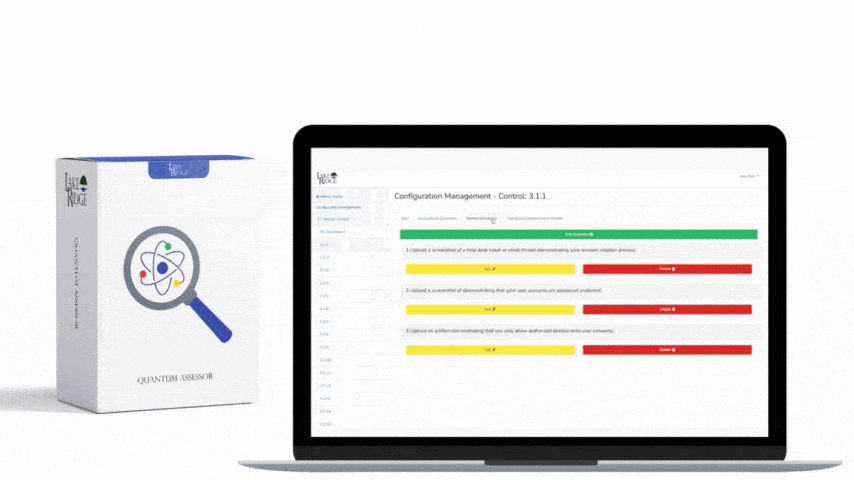
CMMC 1.0 Practice SC.3.182 Requirement:
Prevent unauthorized and unintended information transfer via shared system resources.
CMMC 1.0 SC.3.182 Requirement Explanation:
The control of information in shared resources is commonly referred to as object reuse and residual information protection. This requirement prevents information produced by the actions of prior users from being available to any current users/roles.
Example CMMC 1.0 SC.3.182 Implementation:
Before deploying an operating system to your environment check the Common Criteria website to determine if it is certified. Check to see if it has "object reuse and residual information protection" controls in place. Most popular operating systems are certified and have object reuse controls. Examples include Red Hat Enterprise Linux and Windows 10.
CMMC 1.0 SC.3.182 Scenario(s):
- Scenario 1:
A system administrator wants to use an obscure version of the Linux operating system to setup a server. You search the common criteria website to see if the operating system is certified. Upon discovering that it isn't you instruct the system admin to select a certified operating system for the project.
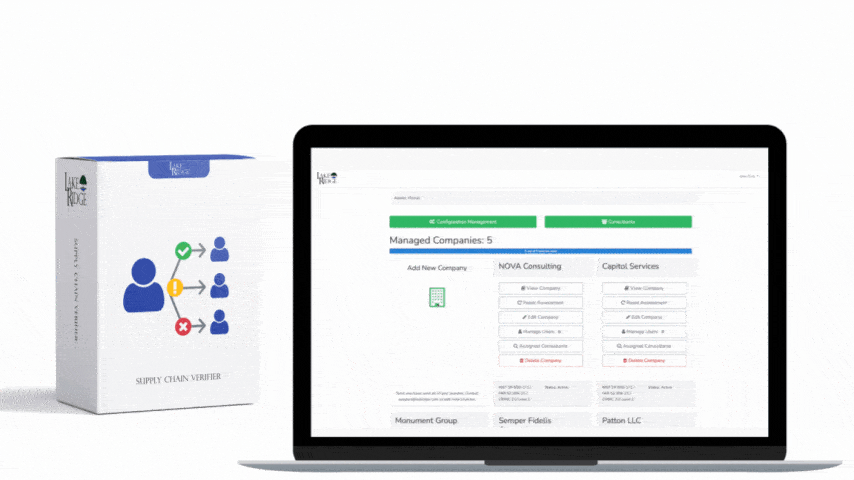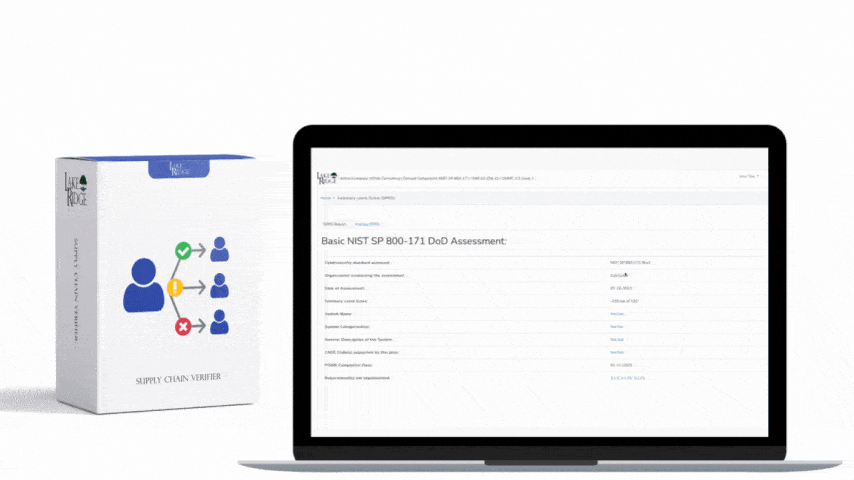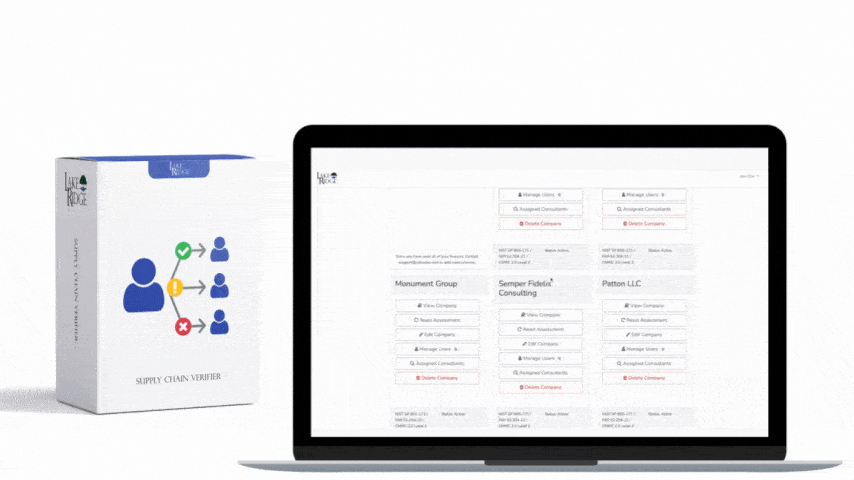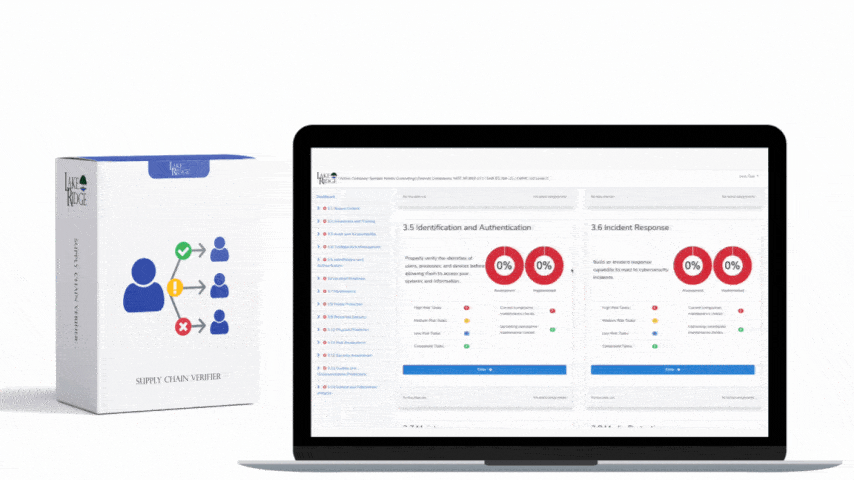
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you