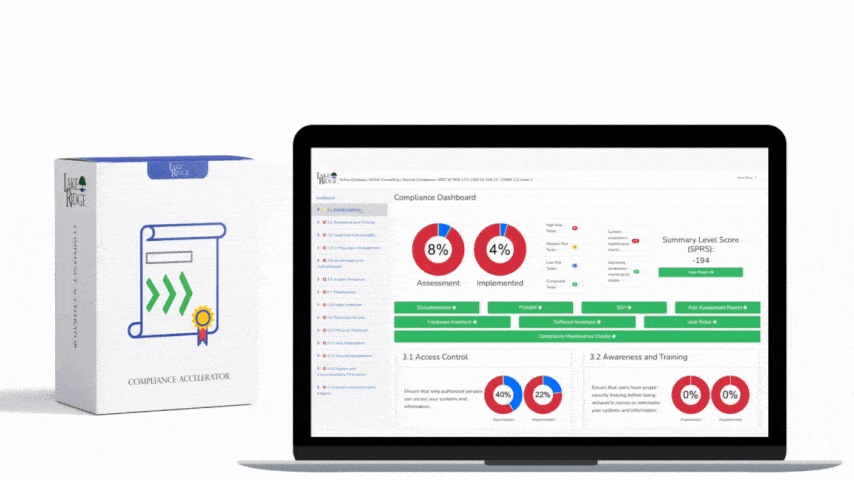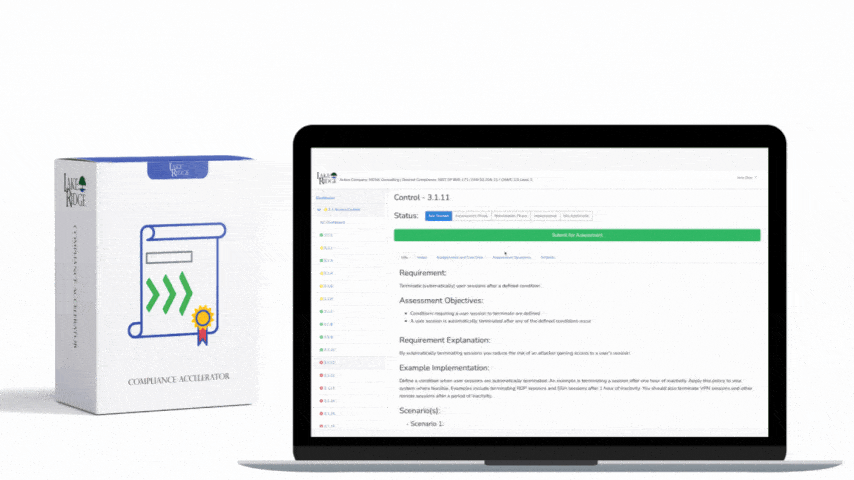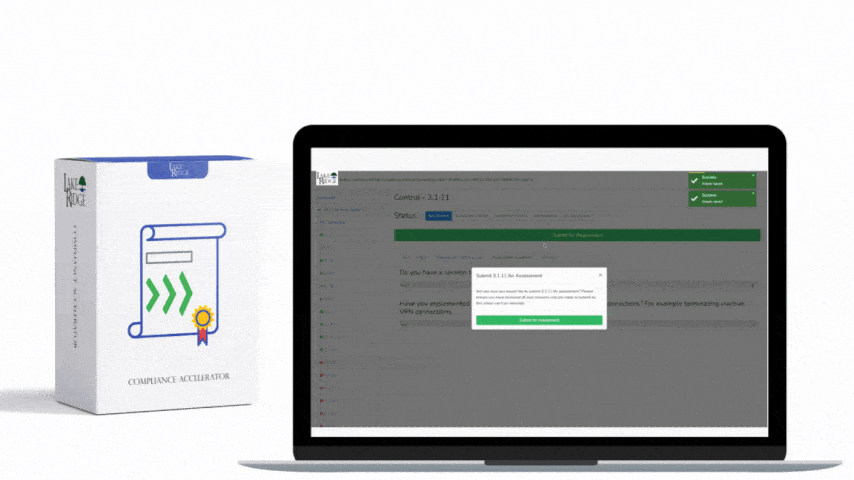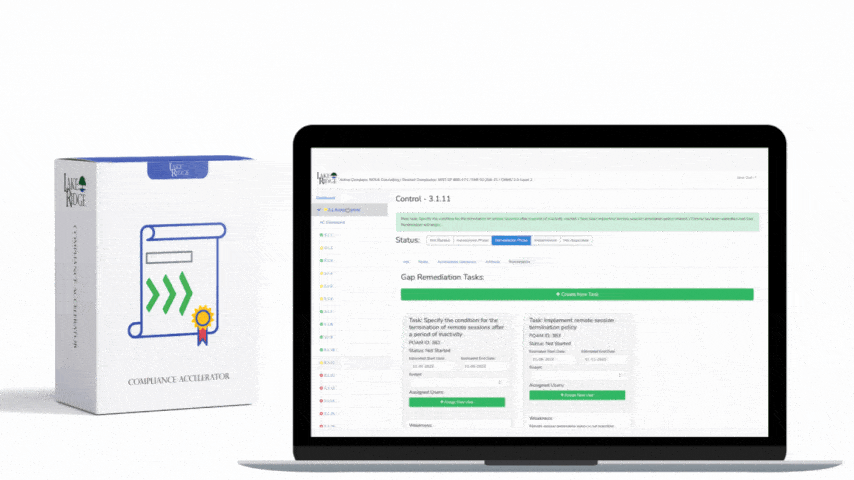
CMMC 1.0 Practice SC.3.183 Requirement:
Deny network communications traffic by default and allow network communications traffic by exception (i.e., deny all, permit by exception).
CMMC 1.0 SC.3.183 Requirement Explanation:
By only allowing authorized traffic in and out of your network you can mitigate a wide range of security threats. This control may be tricky to implement, be sure to carefully plan its implementation.
Example CMMC 1.0 SC.3.183 Implementation:
Only allow authorized traffic in and out of your network. This can be accomplished using firewall rules. This includes blocking ports, IP addresses, and the types of websites users can access. Before blocking traffic, carefully document which traffic needs to come in and out of your network. Document why you have determined to allow some traffic.
CMMC 1.0 SC.3.183 Scenario(s):
- Scenario 1:
Your company wants to limit traffic coming in and out of its network to only traffic required to support your business operations. You analyze the traffic coming in and out of your network to determine the traffic essential for your business operations. You create rules in your firewall to allow this traffic and deny all other traffic.
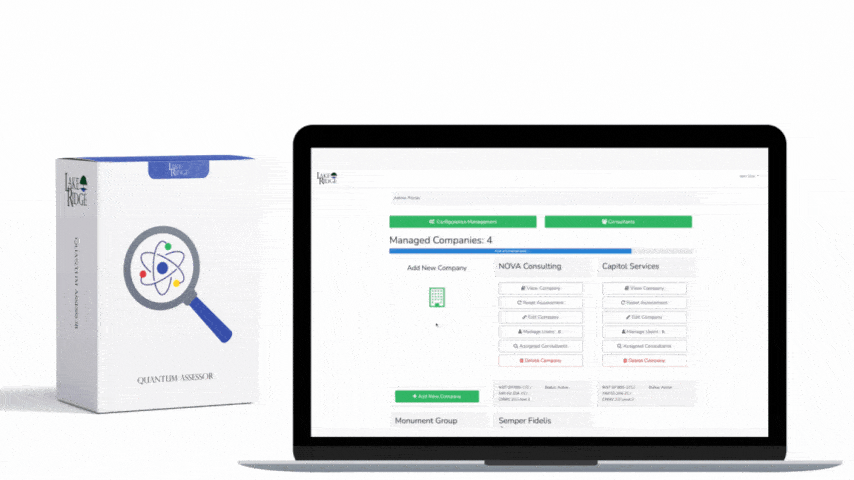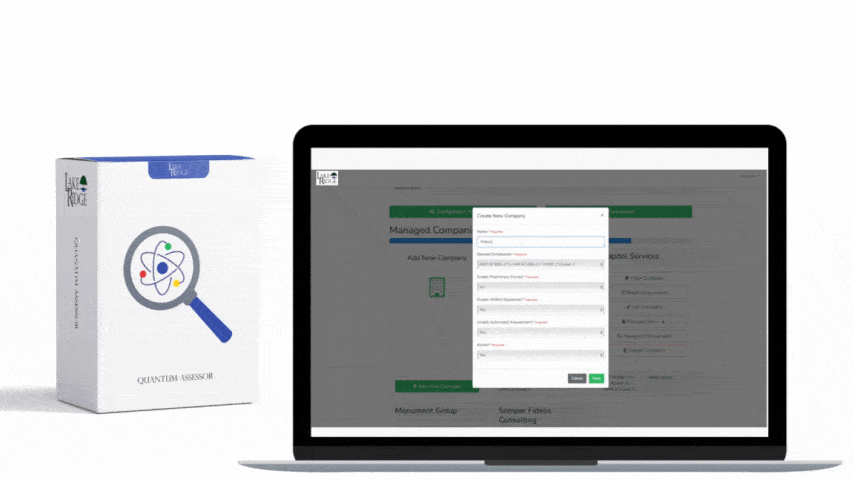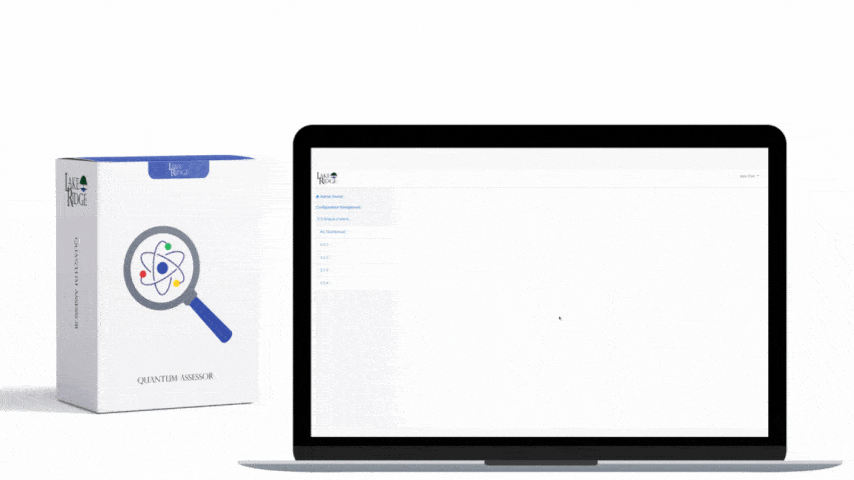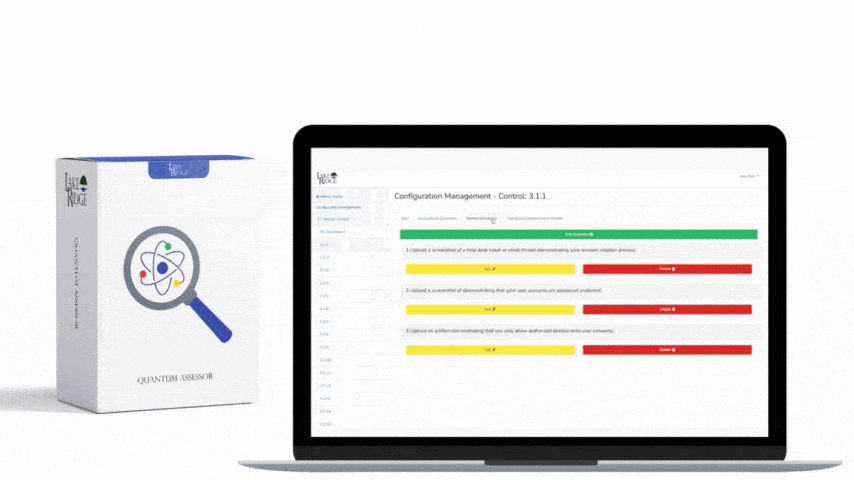
Quick & Simple
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you