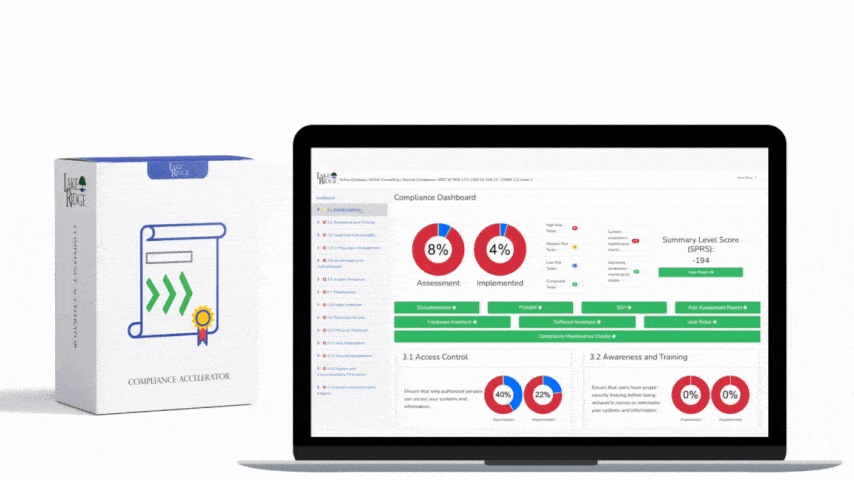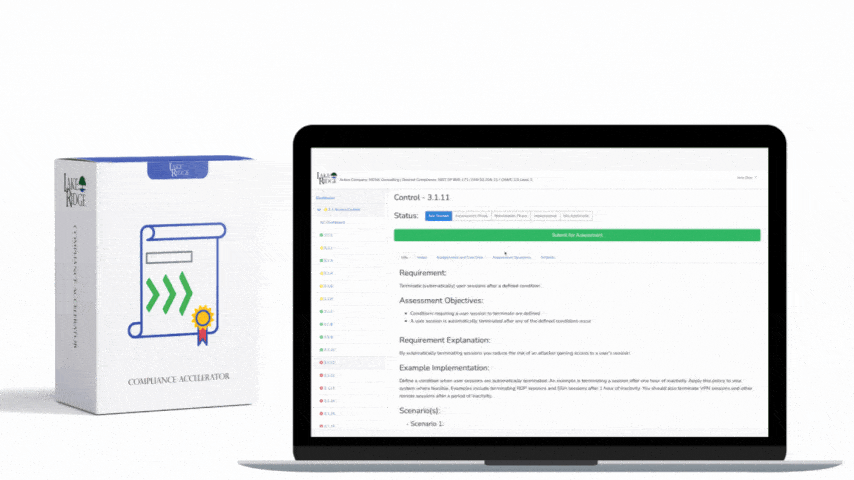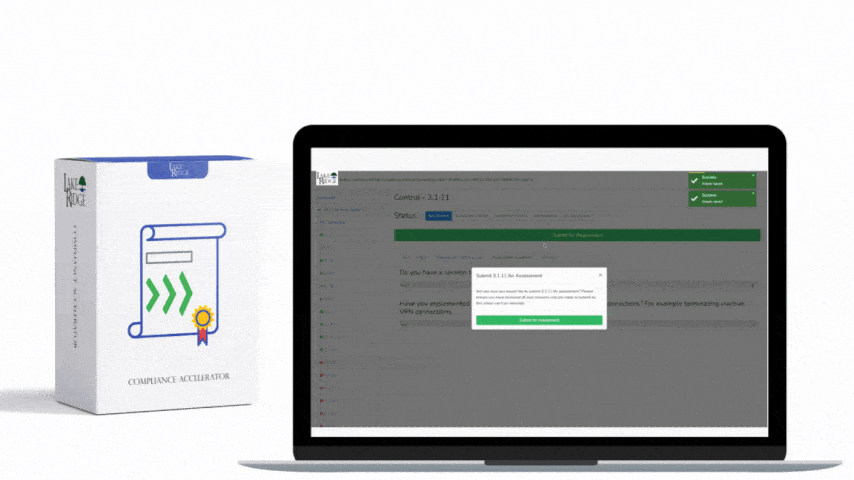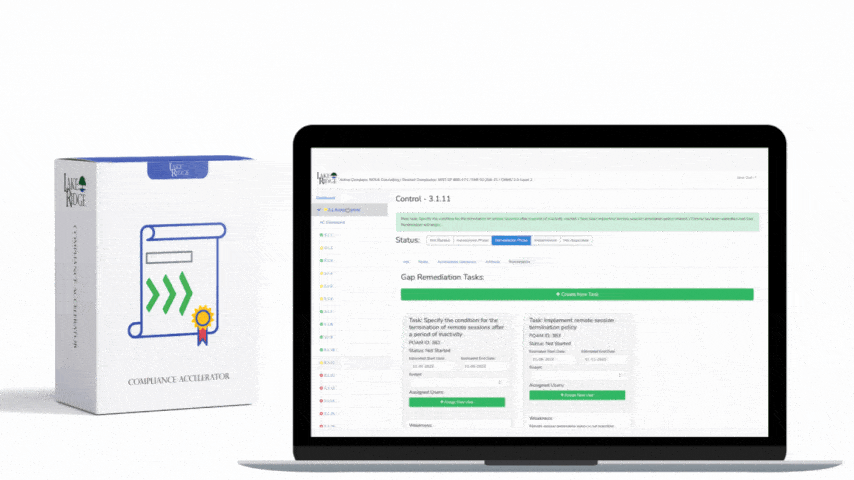
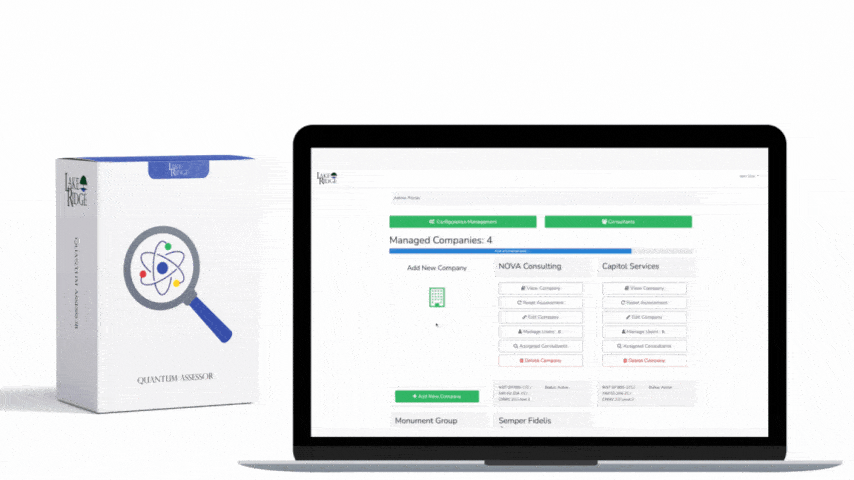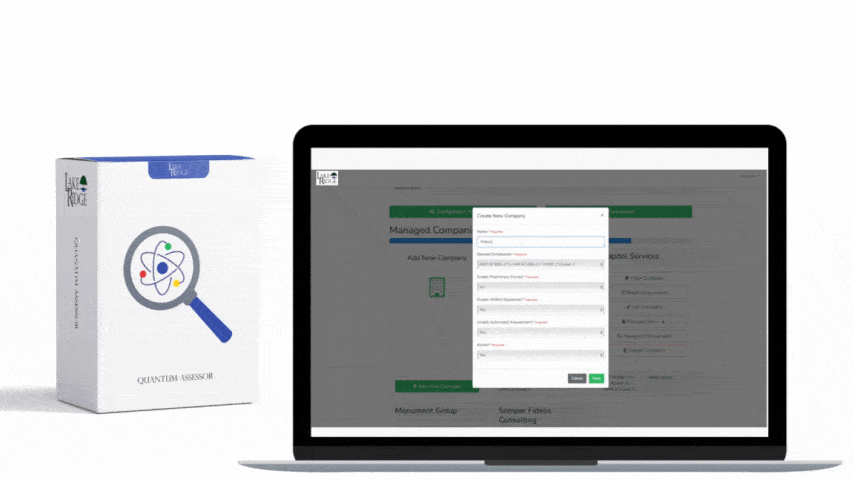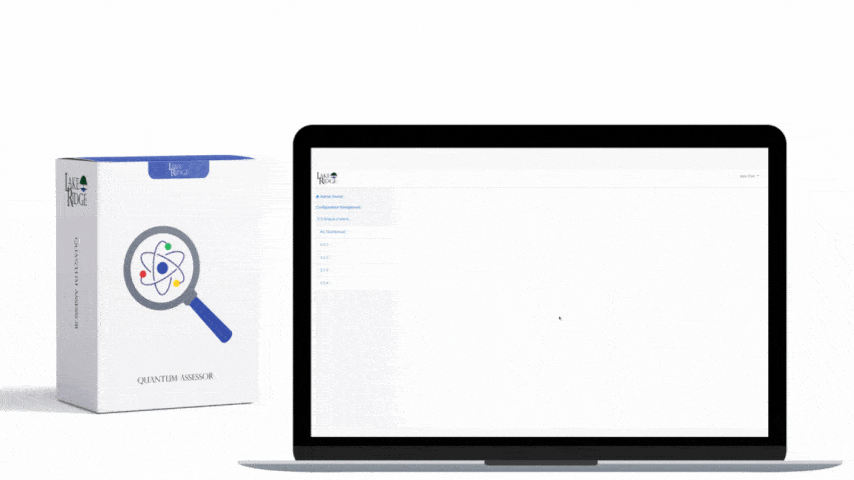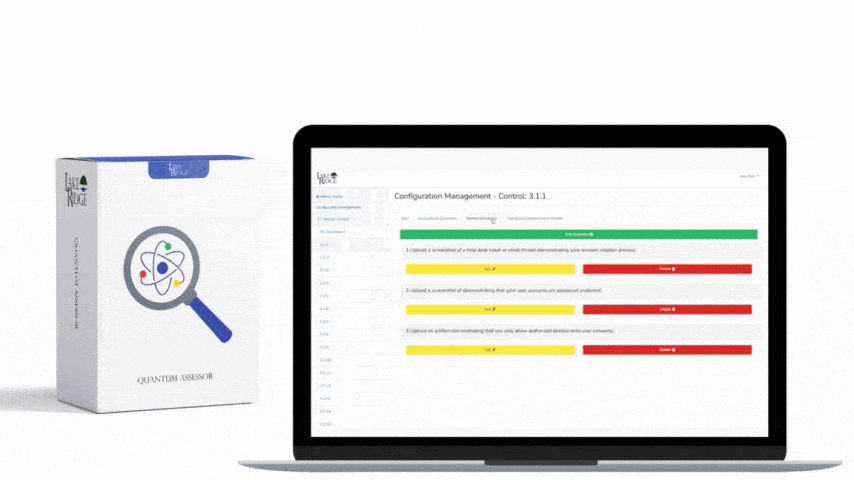
ISO 27001 8.16 Monitoring Activities Requirement:
"Networks, systems and applications shall be monitored for anomalous behaviour and appropriate actions taken to evaluate potential information security incidents."[1]
ISO 27001 8.16 Monitoring Activities Requirement Explanation:
Monitor system alerts and review audit logs to identify security incidents. Alerts are often generated by anti-malware software firewalls network intrusion detection systems and cloud services such as Microsoft 365.
References:
Quick & Simple
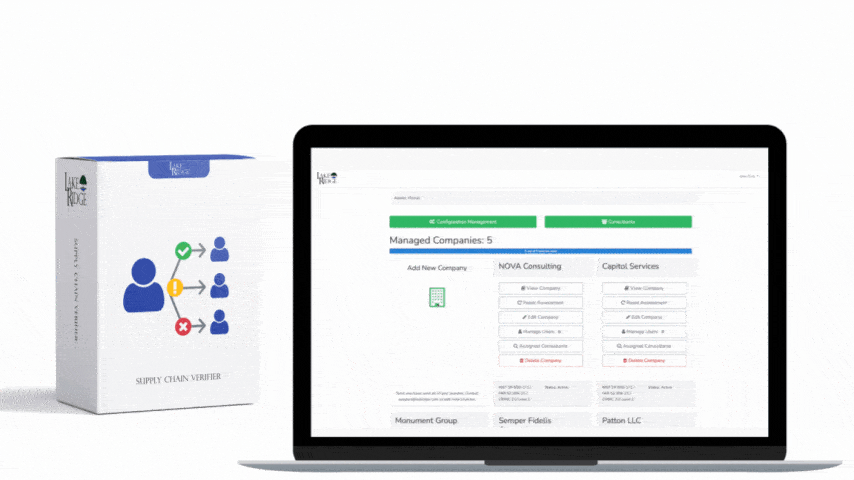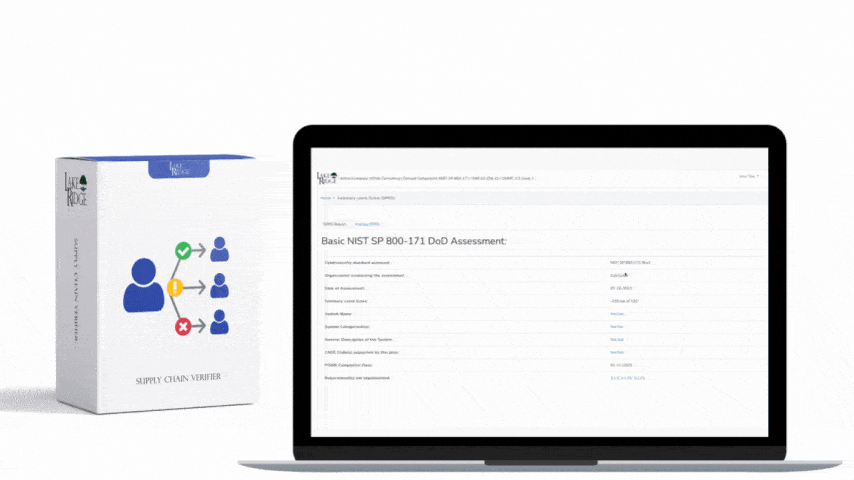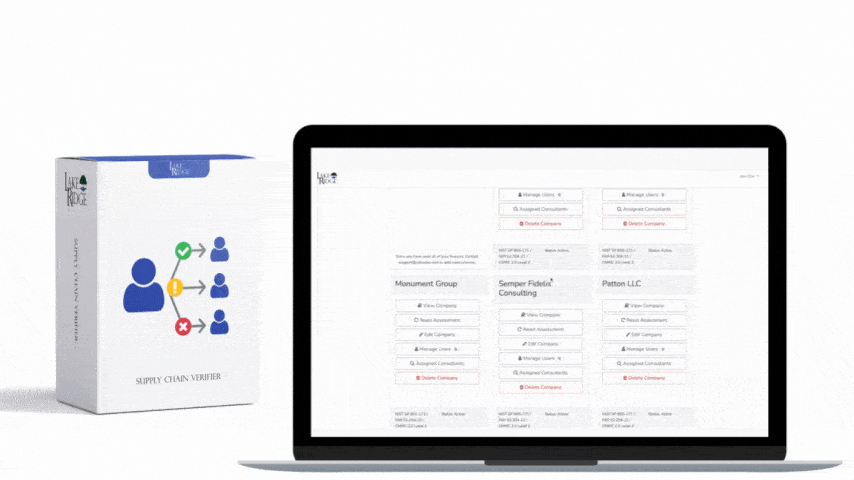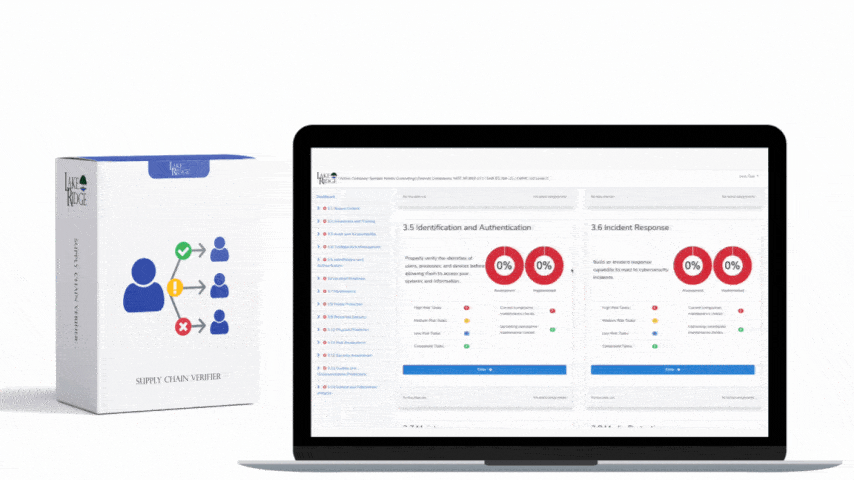
Discover Our Cybersecurity Compliance Solutions:
Whether you need to meet and maintain your compliance requirements, help your clients meet them, or verify supplier compliance we have the expertise and solution for you